- Network
Network
- Bypass firewall
- Network troubleshooting
This is the multi-page printable view of this section. Click here to print.
Some people need to “go home” via public IPv6. Unlike Tailscale/Zerotier et al., which rely on NAT traversal to create direct tunnels, native IPv6 offers a straight-through connection. Cellular networks almost always hand out global IPv6 addresses, so “going home” is extremely convenient.
I previously posted Using Common DDNS Sub-domains on Home Broadband May Downgrade Telecom Service describing a pitfall with IPv6: domains get crawled. Exposing your domain is basically the same as exposing your IPv6 address. Once scanners find open services and inbound sessions pile up, the ISP may silently throttle or downgrade your line.
That thread mentioned domain scanning but not cyberspace scanning—which ignores whatever breadcrumbs you leave and just brute-forces entire address blocks. This is much harder to defend against.
Cyberspace scanning usually includes the following steps:
Below are a few methods to stay off those scanners:
When you browse the web, every outbound connection can leak your source IPv6. If a firewall isn’t in place, that address enters the scanners’ high-priority IP pools.
Even scanning only the last 16 bits of a /56 prefix becomes a smaller task once the prefix is leaked.
After years of IPv6 use, I have seen no practical difference between IPv6 and IPv4 for day-to-day browsing. So we can sacrifice IPv6 for outbound traffic and reserve it solely for “go home” access.
Configure your internal DNS resolver to drop all AAAA answers.
Most home setups run AdGuard Home—see the screenshot:
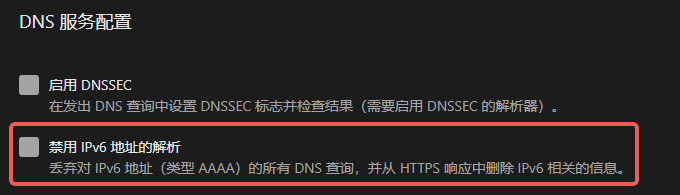
Once applied, local devices reach the outside world over IPv4 only.
Exposing a service on a naked port makes discovery trivial. When you start a service, avoid binding to 0.0.0.0 and ::; almost every tutorial defaults to 127.0.0.1 plus ::1 for good reason—listening on public addresses is risky.
Set server_name to an actual hostname instead of _ or an IP.
server {
listen 80;
server_name yourdomain.com; # replace with your real domain
# 403 for anything not the correct hostname
if ($host != 'yourdomain.com') {
return 403;
}
location / {
root /path/to/your/web/root;
index index.html index.htm;
}
# additional config...
}
Remember to specify the exact hostname—never leave the host field blank.
Create spoofed hostnames that resolve only inside your own DNS.
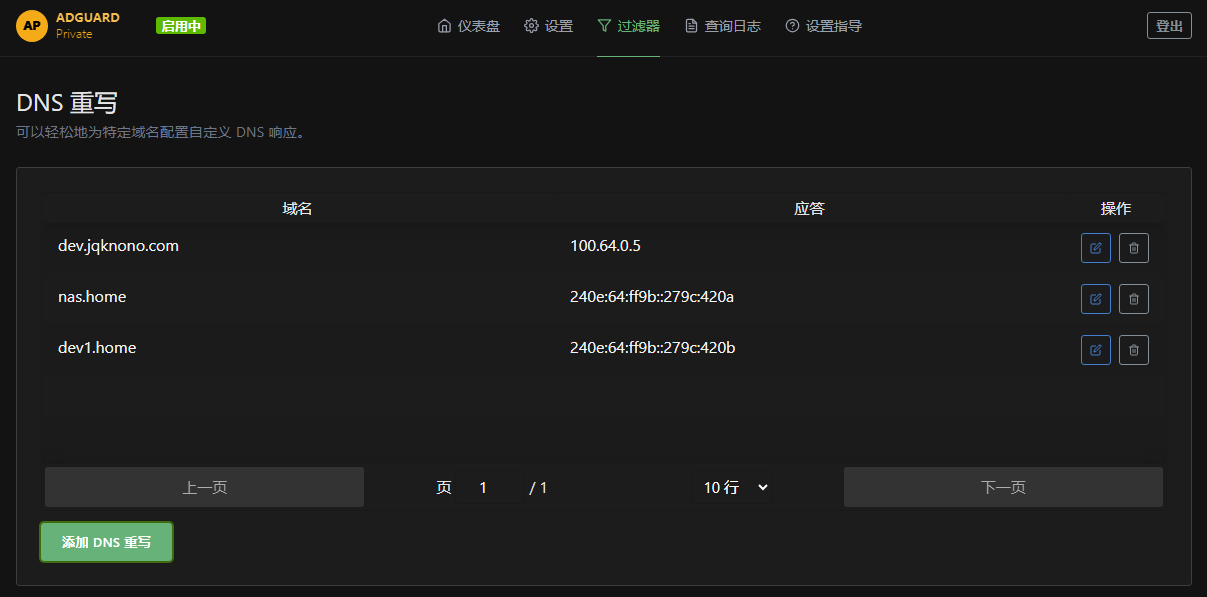
Benefits:
sequenceDiagram
participant Scanner as Scanner
participant DNS as Private DNS
participant Service as Internal Service
Scanner->>DNS: 1. Find private DNS address
Scanner->>DNS: 2. Query fake hostname
DNS-->>Scanner: 3. Return internal IP
Scanner->>Service: 4. Construct Host header
Note right of Service: Denied if Host ≠ fake hostname
alt Correct Host
Service-->>Scanner: 5a. Response
else Wrong Host
Service-->>Scanner: 5b. 403
endThis significantly increases the scanning cost.
You can deploy AdGuardPrivate (almost a labeled AdGuard Home) or Tencent’s dnspod purely for custom records. Functionality differs, so evaluate accordingly.
Prevent the internal DNS from returning AAAA records
Reach internal services only via domain names
Spin up a private DNS
Finally:
I have been troubleshooting IPv6 disconnections and hole-punching failures for over three months. I’ve finally identified the root cause; here’s the story.
IPv6 had been working perfectly. Without touching any settings, and even though every device had its own IPv6, it suddenly lost IPv6 connectivity entirely.
curl 6.ipw.cn returned nothing, and both ping6 and traceroute6 2400:3200::1 failed.
My ONT was bridged to the router, and I could still obtain the router’s own IPv6—one that could still reach the IPv6 Internet.
I received a /56 prefix, and all downstream devices received addresses within 240e:36f:15c3:3200::/56, yet none could reach any IPv6 site.
I suspected the ISP had no route for 240e:36f:15c3:3200::, but I couldn’t prove it.
Someone suggested excessive PCDN upload traffic was the culprit, but upload volume was minimal and PCDN wasn’t enabled.
Another possibility was that using Cloudflare and Aliyun ESA reverse proxies had caused it.
I confirmed that at least some regions of China Telecom will downswitch service when they see many inbound IPv6 HTTP/HTTPS connections, manifesting as:
/56, every device keeps its IPv6, but traceroute lacks a route, so IPv6 is de-facto unusable.Every time I disabled Cloudflare/Aliyun ESA proxying and rebooted the router a few times, both real IPv6 connectivity and true direct Tailscale worked again.
Even with proxy/CDN disabled—complete direct origin access—I still had occasional outages lasting hours.
Perhaps my domain had leaked, or bots were scanning popular subdomains with a steady HTTP attack.
When I disabled DNS resolution for the DDNS hostname outright, IPv6 came back after a while, and Tailscale hole-punching was again direct and stable.
Since then those disconnections never returned.
Avoid using commonplace DDNS subdomains, such as:
I had used several of these; it seems they are continuously scanned by bots. The resulting flood of requests triggered China Telecom’s degradation policy, making my IPv6 unusable and blocking hole-punching.
As you already know, hiding your IP matters in network security; the same goes for protecting the domain you use for DDNS—that domain exposes your IP as well.
If you still need public services, you have two practical choices:
Use Cloudflare’s Tunnel so you won’t see the dozens or hundreds of IPs typical of ordinary reverse proxies.
Build your own VPN, put a VPS in front, and reach your LAN services through the VPN. This avoids excessive simultaneous connections.
Generate a random string—like a GUID—and use it as your DDNS hostname. It’s impossible to remember, but for personal use that’s acceptable. Judge for yourself.
Run your own DNS service, e.g.:
Configure it to serve your DDNS records; only people who can query your private DNS will resolve the custom IP.
In this model you can use common DDNS names, but take care never to expose the address of your private DNS server.
Rumor has it that naming a subdomain speedtest might provide a mysterious boost.
About 90 days ago, I encountered an IPv6 connectivity issue with China Telecom Hubei. After long-term observation and analysis, here are the findings.
Two initial suspected causes:
PCDN usage detection
Home server acting as blog origin
After three months of validation, the issue is more likely triggered by exposing HTTP/HTTPS service ports to the public Internet.
IPv6 anomalies:
Tailscale connection anomalies:
Telecom carriers in certain regions apply service degradation to inbound-heavy HTTP/HTTPS connections:
IPv6 service downgrade
P2P connection throttling
Disable reverse-proxy services:
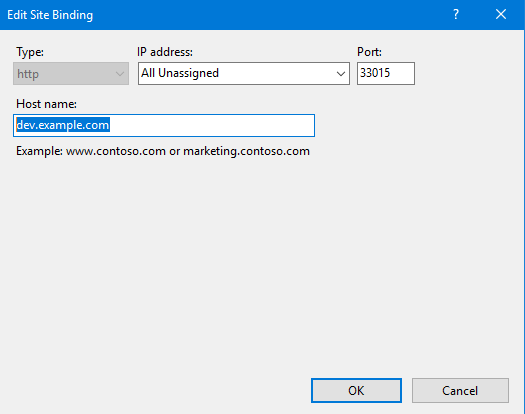
Prevent domain scanning: Avoid these common sub-domains:
- home.example.com
- ddns.example.com
- dev.example.com
- test.example.com
Best practices:
Some Characteristics of China Telecom IPv6
Some Characteristics of China Telecom IPv6
IPv6 has been fully rolled out nationwide; the IPv6 address pool is large enough for each of every individual’s devices to obtain its own IPv6 address.
To actually use IPv6 at home, the entire stack of devices must all support IPv6. Because the rollout has been underway for many years, virtually every device bought after 2016 already supports IPv6.
The full stack includes: metro equipment → community router → home router (ONT/router) → end device (phones, PCs, smart TVs, etc.)
This article does not discuss the standard IPv6 protocol itself; it focuses only on certain characteristics of China Telecom’s IPv6.
First, the methods of address assignment. IPv6 offers three ways to obtain an address: static assignment, SLAAC, and DHCPv6.
Hubei Telecom uses SLAAC, meaning the IPv6 address is automatically assigned by the device. Because the carrier’s IPv6 pool is enormous, address conflicts are impossible.
Telecom IPv6 addresses are assigned at random and recycled every 24 h. If you need inbound access, you must use a DDNS service.
At present it can be observed that common ports such as 80, 139, 445 are blocked—mirroring the carrier’s IPv4 firewall. This is easy to understand: operator-level firewalls do protect ordinary users who lack security awareness. In 2020, China Telecom IPv6 was fully open, but now certain common ports have been blocked.
Port 443 is occasionally accessible within the China Telecom network but blocked for China Mobile and China Unicom. Developers must keep this in mind. A service that works fine in your dev environment—or that your phone on the China Telecom network can reach—may be unreachable from a phone on a different carrier.
Based on simple firewall testing, developers are strongly advised not to trust operator firewalls. Serve your application on a five-digit port.
Furthermore, China Telecom’s firewall does not block port 22, and Windows Remote Desktop port 3389 is likewise open.
Consequently, remote login is possible—introducing obvious risks.
Once attackers obtain the IP or DDNS hostname, they can start targeted attacks; brute-force password cracking can grant control of the device. The domain name can also reveal personal information—name, address, etc.—and attackers may use social-engineering tactics to gather even more clues to speed up their intrusion.
It is recommended to disable password authentication for ssh and rely only on key-based login, or to use a VPN, or to employ a jump host for remote access.
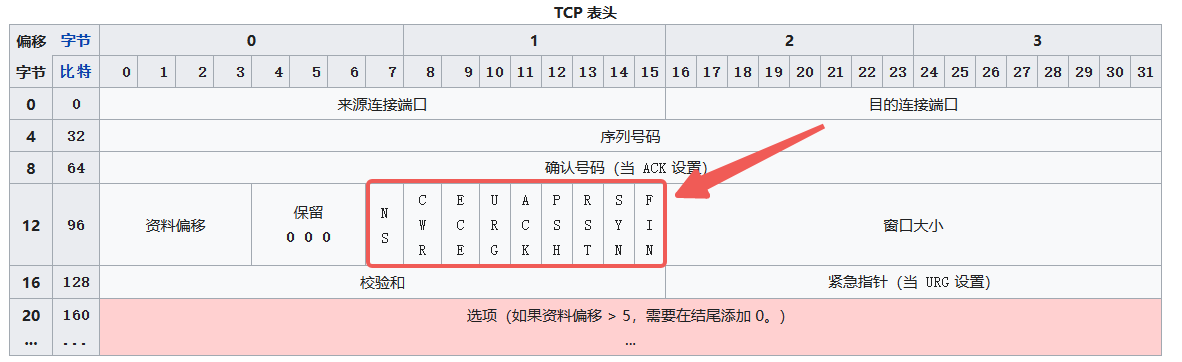
TCP has many concepts: connection establishment, resource usage, data transfer, reliable delivery, retransmission based on cumulative ACK-SACK, timeout retransmission, checksum, flow control, congestion control, MSS, selective acknowledgements, TCP window scale, TCP timestamps, PSH flag, connection termination.
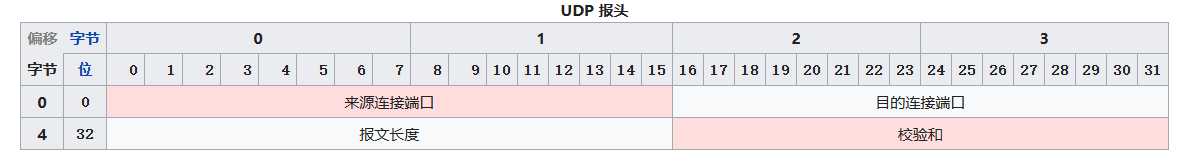
UDP has virtually none of these facilities; it is only slightly more capable than the link layer in distinguishing applications. Because UDP is extremely simple, it is extremely flexible.
Murphy’s law:
If anything can go wrong, it will.
Conventional wisdom suggests that UDP suits games, voice, and video because a few corrupt packets rarely matter. The reason UDP is chosen for these use-cases is not that it is the perfect match, but that there are unsolved problems for TCP that force services to pick the less-featured UDP. Saying “a few corrupt packets do not disturb the service” actually means that TCP worries about packet correctness while UDP does not; UDP cares more about timeliness and continuity. UDP’s defining trait is its indifference to everything TCP considers important—factors that harm real-time performance.
In code, UDP only needs one socket bound to a port to begin sending and receiving. Usually the socket lifetime matches the port lifetime.
Therefore, I can use UDP like this:
Of course none of these patterns can exist in TCP, but in UDP, because they are possible, sooner or later someone will adopt them. Expecting UDP to behave like TCP is therefore idealistic; reality cannot be fully enumerated.
UDP datagrams are extremely lightweight and highly flexible; the idea of a “connection” does not exist at the protocol level, so you must invent your own notion of a UDP connection. Different definitions were tried, yet none could always unambiguously describe direction from a single datagram; we must accept ambiguity. After all, no official “UDP connection” standard exists—when parties hold different definitions, mismatched behaviours are inevitable.
Voice or video can suffer packet loss, but the loss pattern has very different effects on user experience. For example, losing 30 % of packets evenly or losing 30 % all within half a second produces drastically different experiences; the former is obviously preferable. However, UDP has no built-in flow control to deliberately throttle traffic. Although UDP is often described as “best-effort”, the details of that effort still determine the outcome.
For TCP attacks, the client must invest computational resources to create and maintain connections—attackers thus incur costs. With UDP, the attacker’s overhead is much lower; if the goal is just to burn server bandwidth, UDP is perfect. Suppose the service buys 100 GB of unmetered traffic but only processes 10 MB/s while accepting 1 GB/s—90 % of the arriving traffic is junk, yet it is still billable. Providers should avoid such situations.
End-to-end communication comprises multiple endpoints and transit paths. We usually focus only on client and server viewpoints, but the ISP’s perspective matters too. Under DDoS, we pay attention to server capacity, ignoring the ISP’s own finite resources. The server may ignore useless requests, yet the ISP has already paid to carry them. When we perform stress tests we often report “packet loss”, overlooking that the number reflects loss along the entire path—not just at the server. ISPs drop packets as well. From the ISP’s view, the service purchased 1 MB/s, but the client send rate is 1 GB/s; they both pay nothing for the wasted bandwidth—the ISP bears the cost. To avoid that, ISPs implement UDP QoS. Compared to TCP’s congestion control, ISPs can just drop UDP. In practice the blunt approach is to block traffic on long-lived UDP ports. Field tests of WeChat calls show that each call uses multiple ports with one UDP port talking to six different UDP ports on the same server—likely a countermeasure to ISP port blocks.
UDP’s flexibility usually means there are several legitimate methods to reach a goal; as long as the program eventually communicates stably, however bizarre it may appear compared with TCP, it is “the way it is”. We therefore cannot force TCP concepts onto UDP. Even when we invent a new “UDP connection” for product design, we must expect and gracefully accept errors—the ability to tolerate errors is UDP’s core feature, an advantage deliberately chosen by the service, not a flaw we have to live with.
| Tool | Description | Usage | Note |
|---|---|---|---|
| ping | Test network connectivity | ping baidu.com | |
| traceroute | Route tracing | traceroute ip | |
| route | Routing table | route -n | |
| netstat | Network connections | netstat -ano | |
| nslookup | DNS resolution | nslookup baidu.com | |
| ifconfig | Network configuration | ifconfig | |
| arp | ARP cache | arp -a | |
| nbtstat | NetBIOS | nbtstat -n | |
| netsh | Network configuration | netsh | |
| net | Network configuration | net | |
| tcpdump | Packet capture | tcpdump | |
| wireshark | Packet capture | wireshark | |
| ip | Network configuration | ip addr show | |
| ss | Network connections | ss -tunlp | |
| netstat | View network connection state | netstat -anp | |
| tcpdump | Packet-capture utility | tcpdump -i eth0 -nn -s 0 -c 1000 -w /tmp/tcpdump.pcap | |
| iptables | Firewall | iptables -L -n -v -t nat -t mangle -t filter | |
| ss | netstat replacement | ss -anp | |
| ifconfig | View NIC information | ifconfig eth0 | |
| ip | View NIC information | ip addr show eth0 | |
| route | View routing table | route -n | |
| traceroute | View routing hops | traceroute www.baidu.com | |
| ping | Test network connectivity | ping www.baidu.com | |
| telnet | Test port connectivity | telnet www.baidu.com 80 | |
| nslookup | Domain resolution | nslookup www.baidu.com | |
| dig | Domain resolution | dig www.baidu.com | |
| arp | View ARP cache | arp -a | |
| netcat | Network debugging tool | nc -l 1234 | |
| nmap | Port-scanning tool | nmap -sT -p 80 www.baidu.com | |
| mtr | Network connectivity tester | mtr www.baidu.com | |
| iperf | Network performance tester | iperf -s -p 1234 | |
| iptraf | Network traffic monitor | iptraf -i eth0 | |
| ipcalc | IP address calculator | ipcalc | |
| iftop | Network traffic monitor | iftop -i eth0 | |
| iostat | Disk I/O monitor | iostat -x 1 10 | |
| vmstat | Virtual memory monitor | vmstat 1 10 | |
| sar | System performance monitor | sar -n DEV 1 10 | |
| lsof | Show open file usage | lsof -i:80 | |
| strace | Trace system calls | strace -p 1234 | |
| tcpflow | Packet-capture tool | tcpflow -i eth0 -c -C -p -o /tmp/tcpflow | |
| tcpick | Packet-capture tool | tcpick -i eth0 -C -p -o /tmp/tcpick | |
| tcptrace | Packet-capture tool | tcptrace -i eth0 -C -p -o /tmp/tcptrace | |
| tcpslice | Packet-capture tool | tcpslice -i eth0 -C -p -o /tmp/tcpslice | |
| tcpstat | Packet-capture tool | tcpstat -i eth0 -C -p -o /tmp/tcpstat | |
| tcpdump | Packet-capture tool | tcpdump -i eth0 -C -p -o /tmp/tcpdump | |
| tshark | Packet-capture tool | tshark -i eth0 -C -p -o /tmp/tshark | |
| wireshark | Packet-capture tool | wireshark -i eth0 -C -p -o /tmp/wireshark | |
| socat | Network debugging tool | socat -d -d TCP-LISTEN:1234,fork TCP:www.baidu.com:80 | |
| ncat | Network debugging tool | ncat -l 1234 -c ’ncat www.baidu.com 80' | |
| netperf | Network performance tester | netperf -H www.baidu.com -l 60 -t TCP_STREAM | |
| netcat | Network debugging tool | netcat -l 1234 | |
| nc | Network debugging tool | nc -l 1234 | |
| netpipe | Network performance tester | netpipe -l 1234 | |
| netkit | Network debugging tool | netkit -l 1234 | |
| bridge | Bridge tool | bridge -s |
Do nothing, and you’ll already enjoy the best network experience.
First, note that “network quality” and “network experience” are two different concepts. Communication is a process involving many devices. The upload/download performance of a single device can be termed network quality, while the end-to-end behavior of the entire communication path is what we call network experience.
Evaluating network quality usually involves several metrics and methods. Common ones include:
Combined, these indicators give a complete picture of network performance and improvement opportunities. Carriers need these details, but ordinary users often need only a decently priced modern router—today’s devices auto-tune most of these knobs.
The first factor is reachability—being able to connect at all. A DNS service must therefore be:
Next comes the network quality of the resolved IP itself.
Because service quality varies strongly with region, servers geographically closer to the client often offer better performance.
Most paid DNS providers support Geo-aware records. For example, Alibaba Cloud allows:
(1) Carrier lines: Unicom, Telecom, Mobile, CERNet, Great Wall Broadband, Cable WAN—down to province level.
(2) Overseas regions: down to continent and country.
(3) Alibaba cloud lines: down to individual regions.
(4) Custom lines: define any IP range for smart resolution.
“(distribution-map-placeholder)”
By resolving IPs based on location, distant users reach nearby servers automatically—boosting experience without them lifting a finger.
In practice, service providers optimize UX based on the client’s real address. For most users, doing nothing gives the best network experience.
Nearly every Chinese-language guide tells you to pick large authoritative resolvers—Alibaba, Tencent, Cloudflare, Google—because they score high on reachability (comprehensive, accurate, timely). Yet they do not guarantee you the nearest server.
There’s historical context: Chinese ISPs once hijacked DNS plus plaintext HTTP to inject ads. Today, with HTTPS prevalent, this is far less common, though some last-mile ISPs may still try it. Simply switching resolvers to random IPs won’t save you from hijacks directed at UDP 53.
Another user niche cares about content filtering; some providers return bogus IPs for “special” sites. Authoritative resolvers rarely exhibit this behavior.
So three problems arise:
Authoritative resolvers fix (1); encrypted transports (DoT/DoH/QUIC) mitigate (2).
For (3) you must go back to your carrier’s default DNS. As we said: “Do nothing, and you’ll already enjoy the best network experience.”
But if you’re a perfectionist or a special user, the sections below show how to configure AdGuard Home and Clash to satisfy all three concerns at once.
AdGuard Home (ADG) is an ad-blocking, privacy-centric DNS server. It supports custom upstream resolvers and custom rules.
ADG’s default mode is load-balancing: you list several upstreams; ADG weights them by historical response speed and chooses the fastest. In simple terms, it will favor the quickest upstream more often.
Pick the third option instead: “Fastest IP address”.
“(ui-screenshot-placeholder)”
Result: ADG tests the IPs returned by each upstream and replies with whichever has the lowest latency. Below are ordinary results for bilibili.com:
“(ordinary-results-screenshot-placeholder)”
Without this option, ADG would hand every IP back to the client: some apps pick the first, others the last, others pick at random—possibly far from optimal.
With “Fastest IP address” enabled:
“(optimized-results-screenshot-placeholder)”
That alone improves network experience.
Why isn’t “Fastest IP address” the default?
Because waiting for all upstream answers means query time equals the slowest upstream. If you mix a 50 ms Ali server with a 500 ms Google one, your upstream delay becomes ~500 ms.
So users must balance quality vs. quantity. I suggest keeping two upstreams only: one authoritative (https://dns.alidns.com/dns-query) plus your local carrier’s DNS.
Carrier DNS IPs differ by city; look yours up here or read them from your router’s status page:
“(router-dns-screenshot-placeholder)”
Users with special needs who still want optimal routing can delegate DNS handling to Clash’s dns section.
nameserver-policy lets you assign different domains to different resolvers. Example:
dns:
default-nameserver:
- tls://223.5.5.5:853
- tls://1.12.12.12:853
nameserver:
- https://dns.alidns.com/dns-query
- https://one.one.one.one/dns-query
- https://dns.google/dns-query
nameserver-policy:
"geosite:cn,private,apple":
- 202.103.24.68 # your local carrier DNS
- https://dns.alidns.com/dns-query
"geosite:geolocation-!cn":
- https://one.one.one.one/dns-query
- https://dns.google/dns-query
Meaning:
default-nameserver – used solely to resolve hostnames of DNS services in the nameserver list.nameserver – standard resolvers for ordinary queries.nameserver-policy – overrides above resolvers for specific groups of domains.If this post helped you, consider giving it a thumbs-up. Comments and discussion are always welcome!
How to handle the ChatGPT error messages
“Unable to load site”
“Please try again later; if you are using a VPN, try turning it off.”
“Check the status page for information on outages.”
ChatGPT is still the best chatbot in terms of user experience, but in mainland China its use is restricted by the network environment, so we need a proxy (literally a “ladder”) to reach it. ChatGPT is, however, quite strict in detecting proxies, and if it finds one it will simply refuse service. This article explains a way around that detection.
Some people suggest switching IPs to evade a block, yet the geolocations we can get from our providers already belong to supported regions, so this is not necessarily the real reason for denial of service.
Others argue that popular shared proxies are too easy to fingerprint and advise buying more expensive “uncrowded” ones, yet this is hardly a solid argument—IPv4 addresses are scarce, so even overseas ISPs often allocate ports via NAT. Blocking one address would hit a huge community, something that a service as widely used as ChatGPT surely would not design for.
For a public service, checking source-IP consistency makes more sense. Paid proxy plans typically impose data or speed limits, so most users adopt split-routing: they proxy only when the destination is firewalled, letting non-filtered traffic travel directly. This choice of paths can result in inconsistent source IPs. For example, Service A needs to talk to Domains X and Y, yet only X is firewalled; the proxy will be used for X but not Y, so A sees the same request coming from two different IPs.
Solving this source-IP inconsistency will bypass ChatGPT’s “ladder” identification.
Proxy rules usually include domain rules, IP rules, and so on.
Remember that the result of a domain resolution varies by region—if you are in place A you get a nearby server, and in place B you may get another. Therefore, DNS selection matters.
Today there are many DNS protocols; UDP:53 is so outdated and insecure that China lists DNS servers as a top-level requirement for companies. Such rules arose from decades of carriers employing DNS hijacking plus HTTP redirection to insert advertisements, deceiving many non-tech-savvy users and leading to countless complaints. Although today Chrome/Edge automatically upgrade to HTTPS and mark plain HTTP as insecure, many small neighbourhood ISPs and repackaged old Chromium versions persist, so DNS and HTTP hijacking still occur.
Hence we need a safe DNS protocol to avoid hijacking. In my experience Alibaba’s public 223.5.5.5 works well. Of course, when I mention 223.5.5.5 I do not mean plain UDP but DoH or DoT. Configure with tls://223.5.5.5 or https://dns.alidns.com/dns-query.
Alidns rarely gets poisoned—only during certain sensitive periods. You can also use my long-term self-hosted resolver tls://dns.jqknono.com, upstreaming 8.8.8.8 and 1.1.1.1, with cache acceleration.
The detection page first visited runs probing logic, sending requests to several domains to check the source IP, so domain routing must remain consistent.
Besides its own, ChatGPT relies on third-party domains such as auth0, cloudflare, etc.
Add the following rules by hand:
# openai
- DOMAIN-SUFFIX,chatgpt.com,PROXY
- DOMAIN-SUFFIX,openai.com,PROXY
- DOMAIN-SUFFIX,openai.org,PROXY
- DOMAIN-SUFFIX,auth0.com,PROXY
- DOMAIN-SUFFIX,cloudflare.com,PROXY
The domains above may evolve as ChatGPT’s services change; here is how to discover them yourself.
F12 to open DevTools, switch to the Network tab.chat.openai.com or chatgpt.com.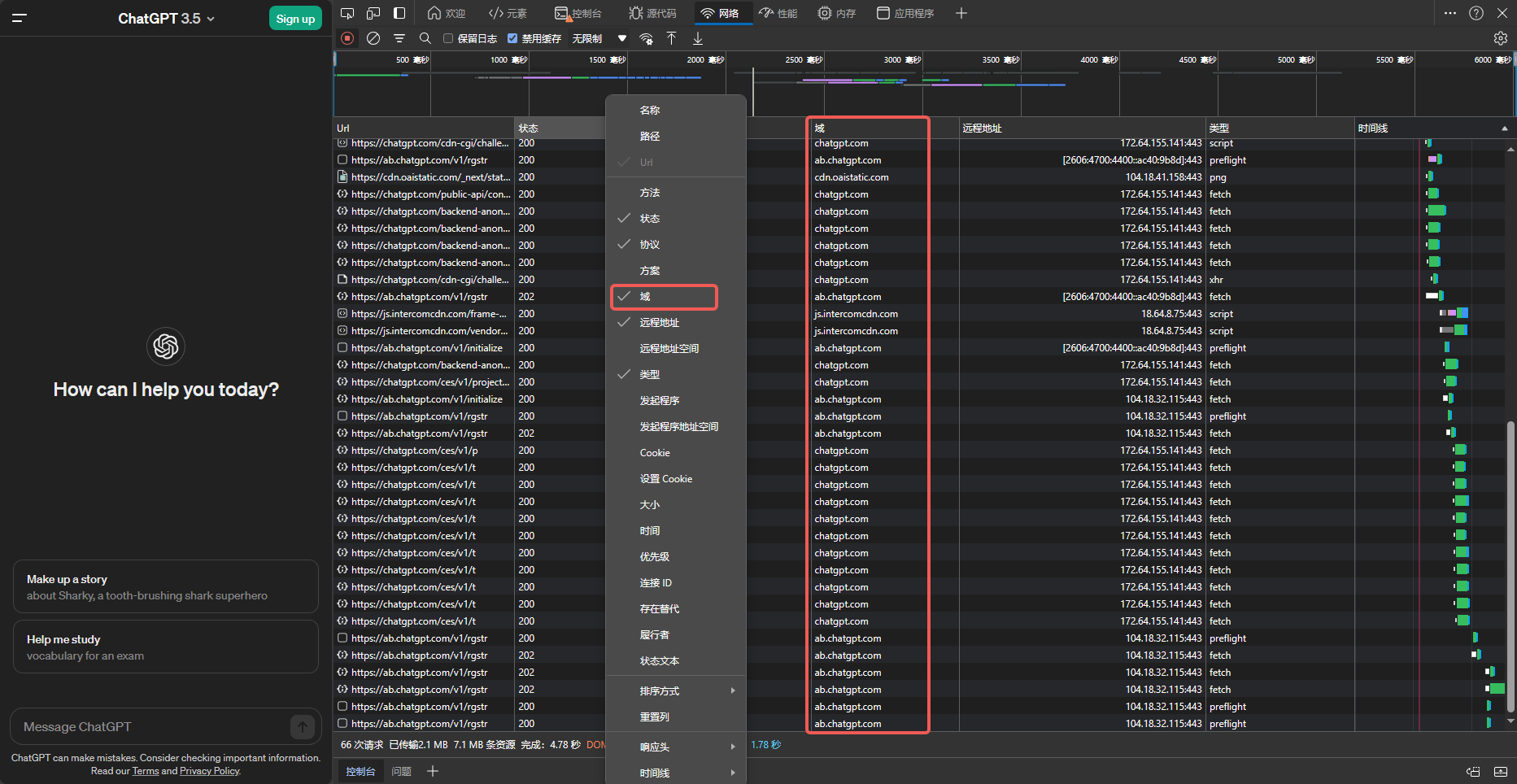
Adding just those domains may still be insufficient. Inspect each aborted request: the challenge response’s Content-Security-Policy lists many domains. Add every one to the proxy policy.
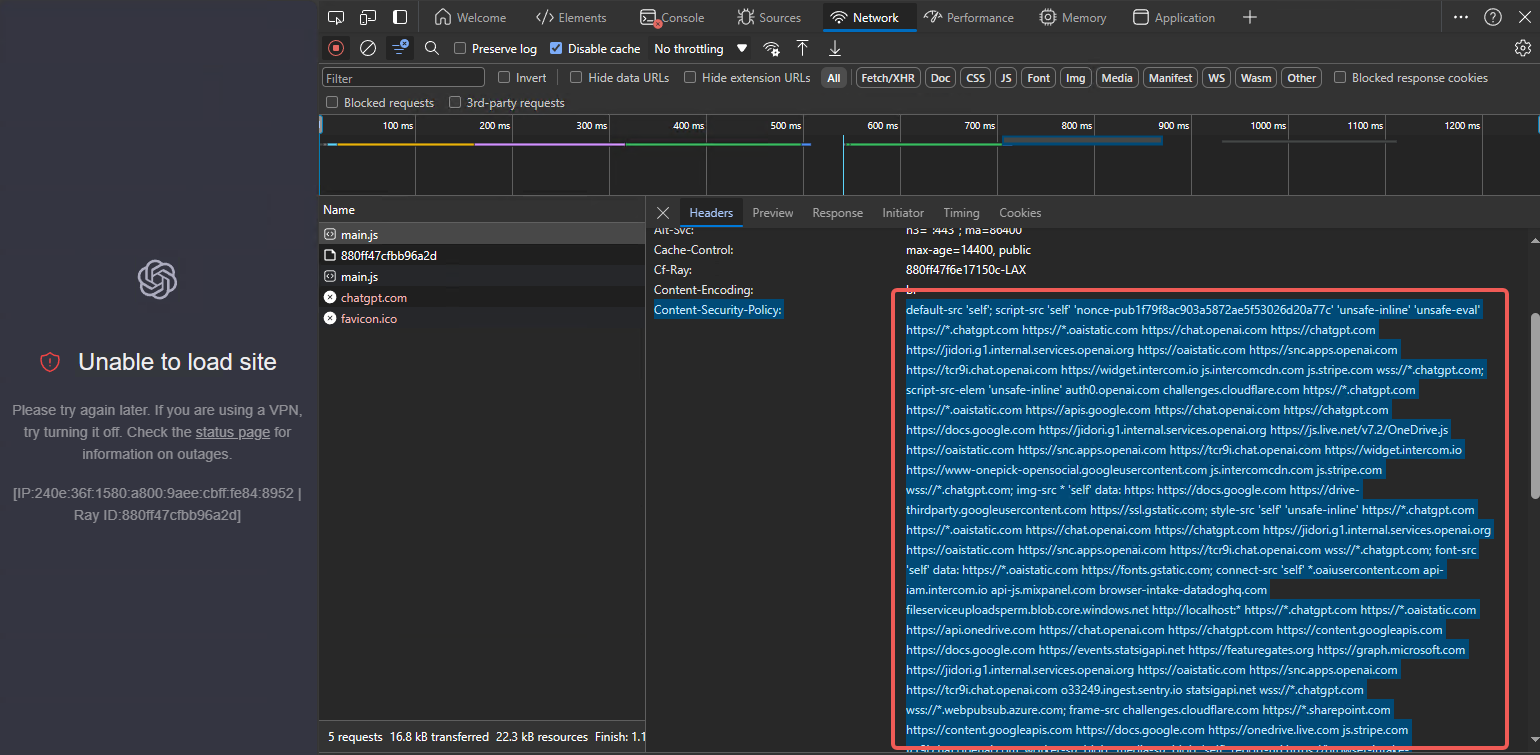
# openai
- DOMAIN-SUFFIX,chatgpt.com,PROXY
- DOMAIN-SUFFIX,openai.com,PROXY
- DOMAIN-SUFFIX,openai.org,PROXY
- DOMAIN-SUFFIX,auth0.com,PROXY
- DOMAIN-SUFFIX,cloudflare.com,PROXY
# additional
- DOMAIN-SUFFIX,oaistatic.com,PROXY
- DOMAIN-SUFFIX,oaiusercontent.com,PROXY
- DOMAIN-SUFFIX,intercomcdn.com,PROXY
- DOMAIN-SUFFIX,intercom.io,PROXY
- DOMAIN-SUFFIX,mixpanel.com,PROXY
- DOMAIN-SUFFIX,statsigapi.net,PROXY
- DOMAIN-SUFFIX,featuregates.org,PROXY
- DOMAIN-SUFFIX,stripe.com,PROXY
- DOMAIN-SUFFIX,browser-intake-datadoghq.com,PROXY
- DOMAIN-SUFFIX,sentry.io,PROXY
- DOMAIN-SUFFIX,live.net,PROXY
- DOMAIN-SUFFIX,live.com,PROXY
- DOMAIN-SUFFIX,windows.net,PROXY
- DOMAIN-SUFFIX,onedrive.com,PROXY
- DOMAIN-SUFFIX,microsoft.com,PROXY
- DOMAIN-SUFFIX,azure.com,PROXY
- DOMAIN-SUFFIX,sharepoint.com,PROXY
- DOMAIN-SUFFIX,gstatic.com,PROXY
- DOMAIN-SUFFIX,google.com,PROXY
- DOMAIN-SUFFIX,googleapis.com,PROXY
- DOMAIN-SUFFIX,googleusercontent.com,PROXY
If the site still refuses to load after the steps above, IP-based detection may also be in play. Below are some IPs I intercepted; they may not fit every region, so test on your own.
# openai
- IP-CIDR6,2606:4700:4400::6812:231c/96,PROXY
- IP-CIDR,17.253.84.253/24,PROXY
- IP-CIDR,172.64.152.228/24,PROXY
- IP-CIDR,104.18.35.28/16,PROXY
Know your proxy tool. Open its connection log, watch the new connections as you reproduce the steps, then add the IPs you see.
A quick guide:
chat.openai.com or chatgpt.com.QUIC is an encrypted UDP protocol, and ChatGPT makes heavy use of QUIC traffic. Therefore both client and server must support UDP forwarding; many do not. Even with support, you must explicitly enable it—some clients default to not proxy UDP traffic. If unsure about UDP, either block QUIC in the proxy client or disable it in the browser; the browser will automatically fall back to HTTP/2 over TCP. QUIC provides smoother performance; feel free to experiment.
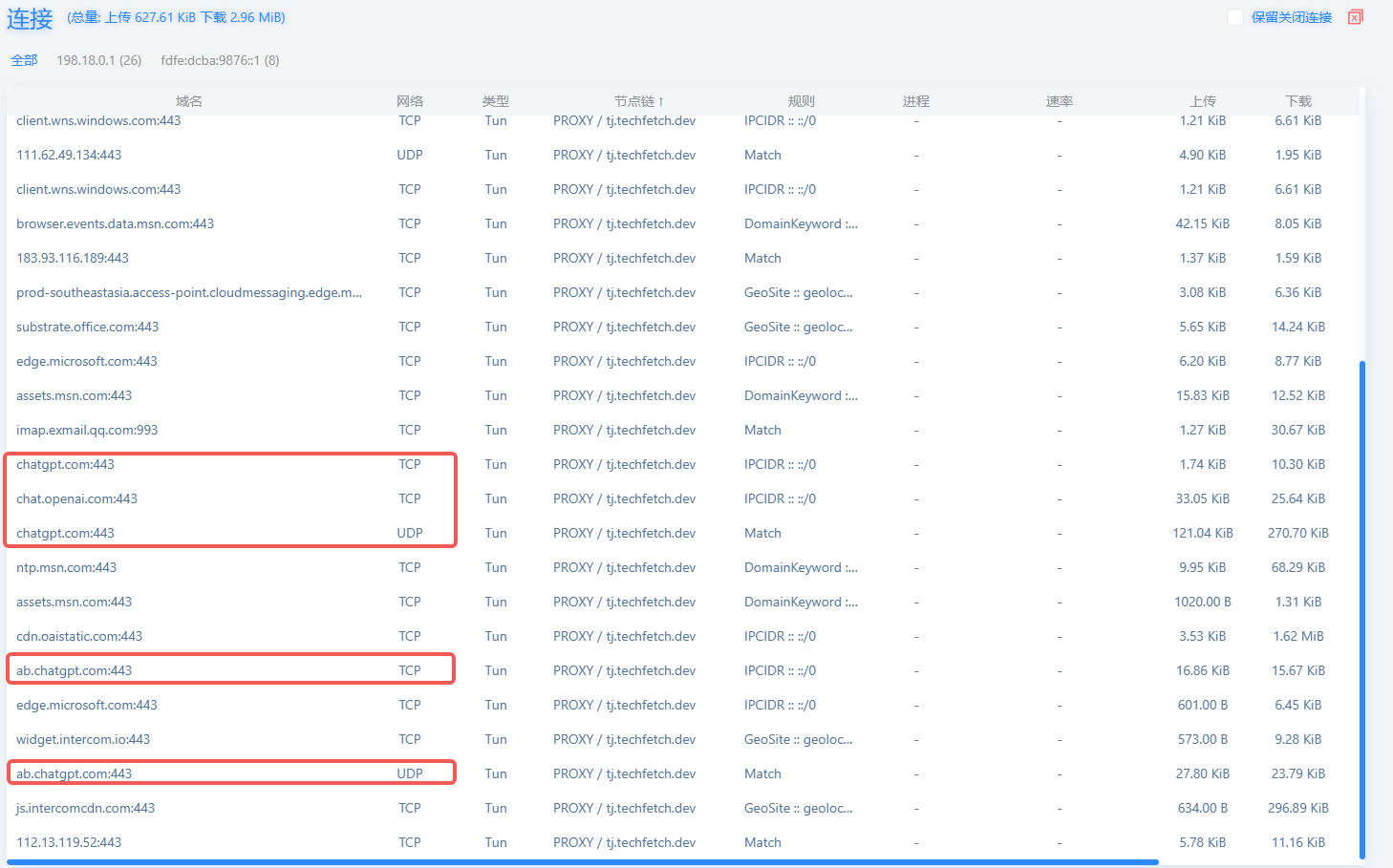
Set direct connections only for Chinese IPs and proxy everything else. This grants reliable ChatGPT access and also covers other foreign services.
The downside is higher data consumption and dependency on your proxy’s quality. If you trust your proxy’s network, give this a shot.
Of course, do remember to enable UDP forwarding.