This is the multi-page printable view of this section. Click here to print.
windows
Windows SSH Remote Login
Enabling SSH remote access on Windows typically requires Windows’ built-in OpenSSH feature. Below are step-by-step instructions:
Check and Install OpenSSH
Check whether OpenSSH is already installed:
- Open Settings > Apps > Apps & features > Manage optional features.
- Look for OpenSSH Server in the list. If found, it is already installed.
Install OpenSSH:
- If OpenSSH Server is not listed, click Add a feature, locate OpenSSH Server in the list, click it, then click Install.
Start and Configure the OpenSSH Service
Start the OpenSSH service:
- After installation, open Command Prompt (run as administrator).
- Type
net start sshdto start the OpenSSH service. To make it start automatically at boot, runsc config sshd start= auto.
Configure the firewall:
- Ensure the Windows firewall allows SSH connections. Go to Control Panel > System and Security > Windows Defender Firewall > Advanced settings, create an inbound rule to allow connections on TCP port 22.
Get the IP Address and Test the Connection
Get the IP address:
- To connect from another machine, you’ll need the IP address of the Windows PC where SSH was enabled. Run
ipconfigat the command prompt to find it.
- To connect from another machine, you’ll need the IP address of the Windows PC where SSH was enabled. Run
Connection test:
- Use an SSH client (e.g., PuTTY, Termius) from another computer or device to connect, using the format
ssh username@your_ip_address, whereusernameis the Windows account name andyour_ip_addressis the address you just obtained.
- Use an SSH client (e.g., PuTTY, Termius) from another computer or device to connect, using the format
Modify Configuration
Avoid logging in with passwords—this is a must-avoid trap. Always use public keys to log in.
We need to disable password login and enable public-key login by adjusting the configuration.
Because the file is protected, editing it requires special privileges, and its folder and file permissions must be set to specific values. Using a script is strongly recommended.
# Check for admin rights
$elevated = [bool]([System.Security.Principal.WindowsPrincipal]::new(
[System.Security.Principal.WindowsIdentity]::GetCurrent()
).IsInRole([System.Security.Principal.WindowsBuiltInRole]::Administrator))
if (-not $elevated) {
Write-Error "Please run this script with administrator rights"
exit 1
}
# 1. Check and install the OpenSSH server if necessary
Write-Host "Checking OpenSSH server installation status..."
$capability = Get-WindowsCapability -Online -Name OpenSSH.Server~~~~0.0.1.0
if ($capability.State -ne 'Installed') {
Write-Host "Installing OpenSSH server..."
Add-WindowsCapability -Online -Name OpenSSH.Server~~~~0.0.1.0 | Out-Null
}
# 2. Start and set the OpenSSH service to auto-start
Write-Host "Configuring SSH service..."
$service = Get-Service sshd -ErrorAction SilentlyContinue
if (-not $service) {
Write-Error "OpenSSH service failed to install"
exit 1
}
if ($service.Status -ne 'Running') {
Start-Service sshd
}
Set-Service sshd -StartupType Automatic
# 3. Edit the configuration file
$configPath = "C:\ProgramData\ssh\sshd_config"
if (Test-Path $configPath) {
Write-Host "Backing up original configuration file..."
Copy-Item $configPath "$configPath.bak" -Force
} else {
Write-Error "Configuration file not found: $configPath"
exit 1
}
Write-Host "Modifying SSH configuration..."
$config = Get-Content -Path $configPath -Raw
# Enable pubkey authentication and disable password login
$config = $config -replace '^#?PubkeyAuthentication .*$','PubkeyAuthentication yes' `
-replace '^#?PasswordAuthentication .*$','PasswordAuthentication no'
# Ensure necessary configs are present
if ($config -notmatch 'PubkeyAuthentication') {
$config += "`nPubkeyAuthentication yes"
}
if ($config -notmatch 'PasswordAuthentication') {
$config += "`nPasswordAuthentication no"
}
# Write the new configuration
$config | Set-Content -Path $configPath -Encoding UTF8
Confirm authorized_keys Permissions
# normal user
$authKeys = "$env:USERPROFILE\.ssh\authorized_keys"
icacls $authKeys /inheritance:r /grant "$($env:USERNAME):F" /grant "SYSTEM:F"
icacls "$env:USERPROFILE\.ssh" /inheritance:r /grant "$($env:USERNAME):F" /grant "SYSTEM:F"
# administrator
$adminAuth = "C:\ProgramData\ssh\administrators_authorized_keys"
icacls $adminAuth /inheritance:r /grant "Administrators:F" /grant "SYSTEM:F"
Set Firewall Rules
# Allow SSH port
New-NetFirewallRule -DisplayName "OpenSSH Server (sshd)" -Direction Inbound -Protocol TCP -Action Allow -LocalPort 22
Add Public Keys
Normal User
# normal user
$userProfile = $env:USERPROFILE
$sshDir = Join-Path $userProfile ".ssh"
$authorizedKeysPath = Join-Path $sshDir "authorized_keys"
$PublicKeyPath = "D:\public_keys\id_rsa.pub"
# Create .ssh directory
if (-not (Test-Path $sshDir)) {
New-Item -ItemType Directory -Path $sshDir | Out-Null
}
# Set .ssh directory permissions
$currentUser = "$env:USERDOMAIN\$env:USERNAME"
$acl = Get-Acl $sshDir
$rule = New-Object System.Security.AccessControl.FileSystemAccessRule(
$currentUser, "FullControl", "ContainerInherit,ObjectInherit", "None", "Allow"
)
$acl.AddAccessRule($rule)
Set-Acl $sshDir $acl
# Add public key
if (Test-Path $PublicKeyPath) {
$pubKey = Get-Content -Path $PublicKeyPath -Raw
if ($pubKey) {
# Ensure newline at end
if (-not $pubKey.EndsWith("`n")) {
$pubKey += "`n"
}
# Append key
Add-Content -Path $authorizedKeysPath -Value $pubKey -Encoding UTF8
# Set file permissions
$acl = Get-Acl $authorizedKeysPath
$acl.SetSecurityDescriptorRule(
(New-Object System.Security.AccessControl.FileSystemAccessRule(
$currentUser, "FullControl", "None", "None", "Allow"
))
)
Set-Acl $authorizedKeysPath $acl
}
} else {
Write-Error "Public key file not found: $PublicKeyPath"
exit 1
}
# Restart SSH service
Write-Host "Restarting SSH service..."
Restart-Service sshd
Administrator User
# administrator
$adminSshDir = "C:\ProgramData\ssh"
$adminAuthKeysPath = Join-Path $adminSshDir "administrators_authorized_keys"
$adminPublicKeyPath = "D:\public_keys\id_rsa.pub"
# Create admin SSH directory
if (-not (Test-Path $adminSshDir)) {
New-Item -ItemType Directory -Path $adminSshDir | Out-Null
}
# Set admin SSH directory permissions
$adminAcl = Get-Acl $adminSshDir
$adminRule = New-Object System.Security.AccessControl.FileSystemAccessRule(
"Administrators", "FullControl", "ContainerInherit,ObjectInherit", "None", "Allow"
)
$adminAcl.AddAccessRule($adminRule)
Set-Acl $adminSshDir $adminAcl
# Add admin public key
if (Test-Path $adminPublicKeyPath) {
$adminPubKey = Get-Content -Path $adminPublicKeyPath -Raw
if ($adminPubKey) {
# Ensure newline at end
if (-not $adminPubKey.EndsWith("`n")) {
$adminPubKey += "`n"
}
# Append key
Add-Content -Path $adminAuthKeysPath -Value $adminPubKey -Encoding UTF8
# Set file permissions
$adminAcl = Get-Acl $adminAuthKeysPath
$adminAcl.SetSecurityDescriptorRule(
(New-Object System.Security.AccessControl.FileSystemAccessRule(
"Administrators", "FullControl", "None", "None", "Allow"
))
)
Set-Acl $adminAuthKeysPath $adminAcl
}
} else {
Write-Error "Admin public key file not found: $adminPublicKeyPath"
exit 1
}
# Restart SSH service
Write-Host "Restarting SSH service..."
Restart-Service sshd
Understanding Windows Networking_WFP
- Understanding Windows Networking_WFP
Understanding Windows Networking
- Understanding Windows Networking
WFP
Terminology
https://learn.microsoft.com/en-us/windows/win32/fwp/object-model
https://learn.microsoft.com/en-us/windows/win32/fwp/basic-operation
https://learn.microsoft.com/en-us/windows-hardware/drivers/network
callout: A callout provides functionality that extends the capabilities of the Windows Filtering Platform. A callout consists of a set of callout functions and a GUID key that uniquely identifies the callout.
callout driver: A callout driver is a driver that registers callouts with the Windows Filtering Platform. A callout driver is a type of filter driver.
callout function: A callout function is a function that is called by the Windows Filtering Platform to perform a specific task. A callout function is associated with a callout.
filter: A filter is a set of functions that are called by the Windows Filtering Platform to perform filtering operations. A filter consists of a set of filter functions and a GUID key that uniquely identifies the filter.
filter engine: The filter engine is the component of the Windows Filtering Platform that performs filtering operations. The filter engine is responsible for calling the filter functions that are registered with the Windows Filtering Platform.
filter layer: A filter layer is a set of functions that are called by the Windows Filtering Platform to perform filtering operations. A filter layer consists of a set of filter layer functions and a GUID key that uniquely identifies the filter layer.
The dispatcher queue triggers callbacks as soon as possible without waiting for the queue to fill, thus satisfying real-time requirements.
When the user callback is slow, blocked packets are inserted into the next queue whenever possible, up to a queue limit of 256. Any additional blocked packets are buffered by the system. Rough testing shows a buffer capacity of around 16,500; this system cache size can vary with machine performance and configuration.
When the user callback processes a packet, there are two packet entities:
- Kernel packet: Released in bulk after the callback finishes processing the queue. Therefore, when the callback is slow, one callback execution can lock up to 256 system packet buffers.
- Copy in callback: Released immediately after the individual packet is processed.
Copying and assembling packets in FwppNetEvent1Callback does not touch the original packets, so business operations remain unaffected.
Subscribing with template filters can reduce the number of packets that need processing:
filterCondition
An array of FWPM_FILTER_CONDITION0 structures containing distinct filter conditions (duplicate filter conditions will produce an error). All conditions must be true for the action to occur; in other words, the conditions are AND’ed together. If no conditions are provided, the action is always performed.
- Identical filters cannot be used.
- The relationship among all filters is logical AND—all must be satisfied.
- Microsoft documentation lists eight supported filters, but in practice many more are supported.
FWPM_CONDITION_IP_PROTOCOL
The IP protocol number, as specified in RFC 1700.
FWPM_CONDITION_IP_LOCAL_ADDRESS
The local IP address.
FWPM_CONDITION_IP_REMOTE_ADDRESS
The remote IP address.
FWPM_CONDITION_IP_LOCAL_PORT
The local transport protocol port number. For ICMP, this is the message type.
FWPM_CONDITION_IP_REMOTE_PORT
The remote transport protocol port number. For ICMP, this is the message code.
FWPM_CONDITION_SCOPE_ID
The interface IPv6 scope identifier; reserved for internal use.
FWPM_CONDITION_ALE_APP_ID
The full path of the application.
FWPM_CONDITION_ALE_USER_ID
The identification of the local user.
Enumerating registered subscriptions shows two existing ones. Their sessionKey GUIDs provide no clues about the registering identity. Analysis shows each implements:
- Subscription to all
FWPM_NET_EVENT_TYPE_CLASSIFY_DROPpackets to collect statistics on dropped packets. - Subscription to all
FWPM_NET_EVENT_TYPE_CLASSIFY_ALLOWpackets for traffic accounting.
Both subscriptions use the condition filter FWPM_CONDITION_NET_EVENT_TYPE (206e9996-490e-40cf-b831-b38641eb6fcb), confirming that more filters can be applied than the eight listed in Microsoft’s documentation.
Further investigation indicates that the user-mode API can only capture drop events. Non-drop events must be obtained via kernel mode, so a micro-segmentation solution cannot use FWPM_CONDITION_NET_EVENT_TYPE to gather events.
Understanding Windows Event Tracing (ETW)
- Understanding Windows Event Tracing (ETW)
Understanding ETW
Some unnecessary information has been filtered out; see the complete documentation at: https://docs.microsoft.com/en-us/windows/win32/etw/event-tracing-portal
Understanding the Basics
https://learn.microsoft.com/en-us/windows/win32/etw/about-event-tracing
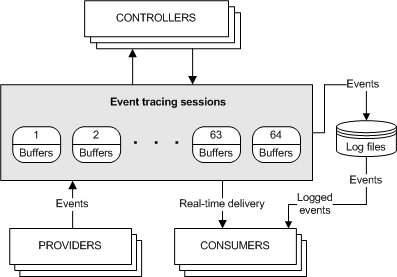
Session
There are four kinds of sessions:
| Session Type | Usage | Limitations | Characteristics |
|---|---|---|---|
| Event Tracing Session(Standard ETW) | 1. EVENT_TRACE_PROPERTIES 2. StartTrace: create a session 3. EnableTrace 1. EnableTrace for classic providers 2. EnableTraceEx for manifest-based providers 4. ControlTrace stop the session | - A manifest-based provider can deliver events to at most 8 sessions. - A classic provider can only serve one session. - The last session to enable a provider supersedes any earlier sessions. | Standard ETW. |
| SystemTraceProvider Session | 1. EVENT_TRACE_PROPERTIES → EnableFlags 2. StartTrace 3. ControlTrace to stop the session | - SystemTraceProvider is a kernel-mode provider that supplies a set of predefined kernel events. - The NT Kernel Logger session is a predefined system session that records a specified set of kernel events. - Windows 7/Windows Server 2008 R2 only the NT Kernel Logger session may use SystemTraceProvider. - Windows 8/Windows Server 2012 SystemTraceProvider can feed 8 logger sessions, two of which are reserved for NT Kernel Logger and Circular Kernel Context Logger. - Windows 10 20348 and later, individual System providers can be controlled separately. | Obtain kernel predefined events. |
| AutoLogger Session | 1. Edit the registry 2. EnableTraceEx 3. ControlTrace to stop the session | - The Global Logger Session is a special, standalone session that records events during system boot. - Ordinary AutoLogger sessions must explicitly enable providers; Global Logger does not. - AutoLogger does not support NT Kernel Logger events; only Global Logger does. - Impacts boot time—use sparingly. | Record OS boot-time events. |
| Private Logger Session | — | - User-mode ETW - Used only within a process - Not counted toward the 64-session concurrency limit. | Per-process only. |
Tools
- logman
- wevtutil
- XPath query example:
wevtutil qe Security /c:2 /q:"*[System[EventID=5157]]" /f:text
- XPath query example:
- tracelog
- To use the Visual Studio
tracelogtool, you can dynamically add and remove ETW Providers and ETW Sessions at runtime.
- To use the Visual Studio
- mc
- etw-providers-docs
wireguard configuration
- wireguard configuration
wireguard Configuration
Firewall Configuration
wireguard /installtunnelservice <wg_conf_path>
wg show
Get-NetConnectionProfile
Get-NetAdapter
Get-NetFirewallProfile
Set-NetFirewallProfile -Profile domain,public,private -DisabledInterfaceAliases <wg_config_name>
Set-NetIPInterface -ifindex <interface index> -Forwarding Enabled
New-NetFirewallRule -DisplayName "@wg1" -Direction Inbound -RemoteAddress 10.66.66.1/24 -Action Allow
New-NetFirewallRule -DisplayName "@wg1" -Direction Outbound -RemoteAddress 10.66.66.1/24 -Action Allow
# Locate the blocking cause
auditpol /set /subcategory:"{0CCE9225-69AE-11D9-BED3-505054503030}" /success:disable /failure:enable
wevtutil qe Security /q:"*[System/EventID=5152]" /c:5 /rd:true /f:text
auditpol /set /subcategory:"{0CCE9225-69AE-11D9-BED3-505054503030}" /success:disable /failure:disable
Windows Blocking Network Traffic Capture
- Windows Blocking Network Traffic Capture
Windows Blocking Network Traffic Capture
- Windows Blocking Network Traffic Capture
- Need to identify blocked traffic, including outbound and inbound.
- Two ways of blocking: by connection or by packet. Packet drops occur frequently and the reason must be audited; connection‐oriented blocks align better with real-world monitoring.
- Many normally processed packets may also be dropped, so we must distinguish drops from actual blocks—we focus on blocks.
Setting Up a Test Project
WFP mainly runs in user mode and partly in kernel mode, exposed as drivers. The test setup is complex.
Recommended: run a separate physical machine for testing, compile on the dev box, then copy and remotely debug on the test machine.
For those with limited resources, local debugging on the same machine is also possible.
- Microsoft WFP Sample Project
- Focus only on: Windows-driver-samples\network\trans\WFPSampler
- WFPSampler Guide
Build Issues:
Other Issues:
Capturing Block Events via Auditing
By default, auditing for WFP is off.
- Audit can be enabled by category (via Group Policy Object Editor MMC, Local Security Policy MMC, or auditpol.exe).
- Audit can also be enabled by subcategory with auditpol.exe.
- Always use GUIDs—otherwise localized display strings break cross-language systems.
- Audit uses circular logs of 128 KB—low resource impact.
Categories https://docs.microsoft.com/en-us/windows/win32/secauthz/auditing-constants
| Category/Subcategory | GUID |
|---|---|
| … | … |
| Object Access | {6997984A-797A-11D9-BED3-505054503030} |
| Policy Change | {6997984D-797A-11D9-BED3-505054503030} |
| … | … |
Object Access subcategories and their GUIDs https://docs.microsoft.com/en-us/openspecs/windows_protocols/ms-gpac/77878370-0712-47cd-997d-b07053429f6d
| Object Access Subcategory | Subcategory GUID | Inclusion Setting |
|---|---|---|
| … | … | … |
| Filtering Platform Packet Drop | {0CCE9225-69AE-11D9-BED3-505054503030} | No Auditing |
| Filtering Platform Connection | {0CCE9226-69AE-11D9-BED3-505054503030} | No Auditing |
| Other Object Access Events | {0CCE9227-69AE-11D9-BED3-505054503030} | No Auditing |
| … | … | … |
Policy Change subcategories and GUIDs:
| Policy Change Subcategory | Subcategory GUID |
|---|---|
| Audit Policy Change | {0CCE922F-69AE-11D9-BED3-505054503030} |
| Authentication Policy Change | {0CCE9230-69AE-11D9-BED3-505054503030} |
| Authorization Policy Change | {0CCE9231-69AE-11D9-BED3-505054503030} |
| MPSSVC Rule-Level Policy Change | {0CCE9232-69AE-11D9-BED3-505054503030} |
| Filtering Platform Policy Change | {0CCE9233-69AE-11D9-BED3-505054503030} |
| Other Policy Change Events | {0CCE9234-69AE-11D9-BED3-505054503030} |
# auditpol reference: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/auditpol
# This section focuses on the 'Object Access' category
# List available fields
# -v shows GUID, -r produces CSV report
auditpol /list /category /v
auditpol /list /subcategory:* /v
# Get audit settings for a subcategory
auditpol /get /category:'Object Access' /r | ConvertFrom-Csv | Get-Member
# Query subcategory GUID
auditpol /get /category:'Object Access' /r | ConvertFrom-Csv | Format-Table Subcategory,'Subcategory GUID','Inclusion Setting'
# Lookup subcategory
auditpol /list /subcategory:"Object Access","Policy Change" -v
# Backup
auditpol /backup /file:d:\audit.bak
# Restore
auditpol /restore /file:d:\audit.bak
# Modify Policy
# **Policy Change** | {6997984D-797A-11D9-BED3-505054503030}
auditpol /set /category:"{6997984D-797A-11D9-BED3-505054503030}" /success:disable /failure:disable
# Filtering Platform Policy Change | {0CCE9233-69AE-11D9-BED3-505054503030}
auditpol /set /subcategory:"{0CCE9233-69AE-11D9-BED3-505054503030}" /success:enable /failure:enable
# **Object Access** | {6997984A-797A-11D9-BED3-505054503030}
auditpol /get /category:"{6997984A-797A-11D9-BED3-505054503030}"
auditpol /set /category:"{6997984A-797A-11D9-BED3-505054503030}" /success:disable /failure:disable
# Filtering Platform Packet Drop | {0CCE9225-69AE-11D9-BED3-505054503030}
auditpol /set /subcategory:"{0CCE9225-69AE-11D9-BED3-505054503030}" /success:disable /failure:enable
# Filtering Platform Connection | {0CCE9226-69AE-11D9-BED3-505054503030}
auditpol /set /subcategory:"{0CCE9226-69AE-11D9-BED3-505054503030}" /success:disable /failure:enable
# Read audit logs
$Events = Get-WinEvent -LogName 'Security'
foreach ($event in $Events) {
ForEach ($line in $($event.Message -split "`r`n")) {
Write-Host $event.RecordId ':' $Line
break
}
}
Event Details:
| Event ID | Explanation |
|---|---|
| 5031(F) | The Windows Firewall Service blocked an application from accepting incoming connections on the network. |
| 5150(-) | The Windows Filtering Platform blocked a packet. |
| 5151(-) | A more restrictive Windows Filtering Platform filter has blocked a packet. |
| 5152(F) | The Windows Filtering Platform blocked a packet. |
| 5153(S) | A more restrictive Windows Filtering Platform filter has blocked a packet. |
| 5154(S) | The Windows Filtering Platform has permitted an application or service to listen on a port for incoming connections. |
| 5155(F) | The Windows Filtering Platform has blocked an application or service from listening on a port for incoming connections. |
| 5156(S) | The Windows Filtering Platform has permitted a connection. |
| 5157(F) | The Windows Filtering Platform has blocked a connection. |
| 5158(S) | The Windows Filtering Platform has permitted a bind to a local port. |
| 5159(F) | The Windows Filtering Platform has blocked a bind to a local port. |
Events to Focus On:
- Audit Filtering Platform Packet Drop
These events generate huge volumes; focus on 5157, which records almost the same data but per-connection rather than per-packet.
Failure volume is typically very high for this subcategory and mainly useful for troubleshooting. To monitor blocked connections, 5157(F): The Windows Filtering Platform has blocked a connection is recommended since it contains nearly identical information and generates per-connection instead of per-packet.
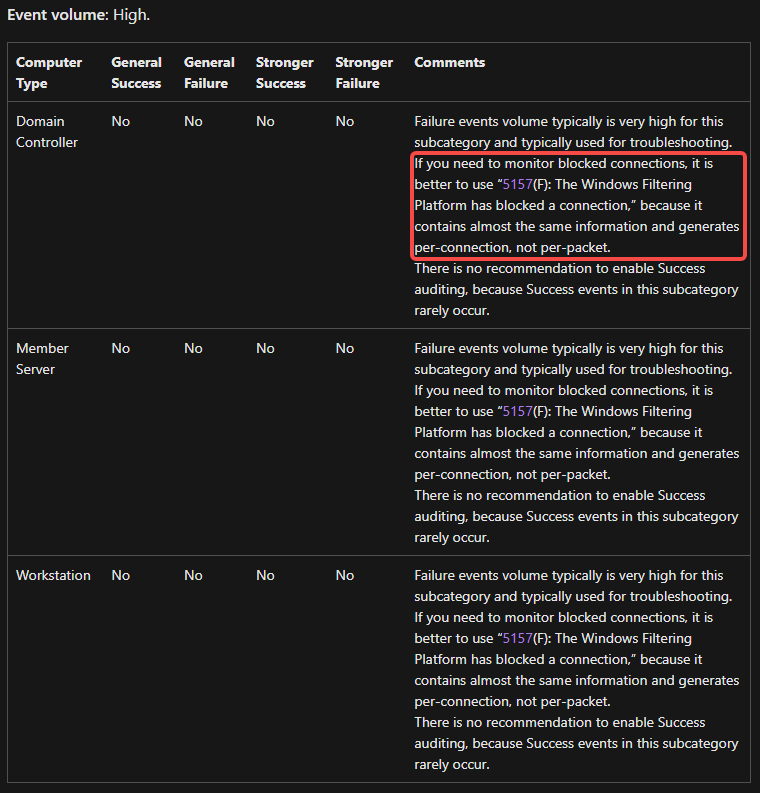
- Audit Filtering Platform Connection
- It is best to monitor only failure events such as blocked connections; track allowed connections only when necessary.
- 5031
- If there are no firewall rules (Allow or Deny) for a specific application in Windows Firewall, traffic will be dropped at the WFP layer, which by default denies all inbound connections.
51505151- 5155
- 5157
- 5159
Obtaining Provider Information
# List security-related providers
Get-WinEvent -ListProvider "*Security*" | Select-Object ProviderName,Id
# Microsoft-Windows-Security-Auditing 54849625-5478-4994-a5ba-3e3b0328c30d
# Show tasks for a provider
Get-WinEvent -ListProvider "Microsoft-Windows-Security-Auditing" | Select-Object -ExpandProperty tasks
# SE_ADT_OBJECTACCESS_FIREWALLCONNECTION 12810 Filtering Platform Connection 00000000-0000-0000-0000-000000000000
| ProviderName | Id |
|---|---|
| Security Account Manager | 00000000-0000-0000-0000-000000000000 |
| Security | 00000000-0000-0000-0000-000000000000 |
| SecurityCenter | 00000000-0000-0000-0000-000000000000 |
| Microsoft-Windows-Security-SPP-UX-GenuineCenter-Logging | fb829150-cd7d-44c3-af5b-711a3c31cedc |
| Microsoft-Windows-Security-Mitigations | fae10392-f0af-4ac0-b8ff-9f4d920c3cdf |
| Microsoft-Windows-VerifyHardwareSecurity | f3f53c76-b06d-4f15-b412-61164a0d2b73 |
| Microsoft-Windows-SecurityMitigationsBroker | ea8cd8a5-78ff-4418-b292-aadc6a7181df |
| Microsoft-Windows-Security-Adminless | ea216962-877b-5b73-f7c5-8aef5375959e |
| Microsoft-Windows-Security-Vault | e6c92fb8-89d7-4d1f-be46-d56e59804783 |
| Microsoft-Windows-Security-Netlogon | e5ba83f6-07d0-46b1-8bc7-7e669a1d31dc |
| Microsoft-Windows-Security-SPP | e23b33b0-c8c9-472c-a5f9-f2bdfea0f156 |
| Microsoft-Windows-Windows Firewall With Advanced Security | d1bc9aff-2abf-4d71-9146-ecb2a986eb85 |
| Microsoft-Windows-Security-SPP-UX-Notifications | c4efc9bb-2570-4821-8923-1bad317d2d4b |
| Microsoft-Windows-Security-SPP-UX-GC | bbbdd6a3-f35e-449b-a471-4d830c8eda1f |
| Microsoft-Windows-Security-Kerberos | 98e6cfcb-ee0a-41e0-a57b-622d4e1b30b1 |
| Microsoft-Windows-Security-ExchangeActiveSyncProvisioning | 9249d0d0-f034-402f-a29b-92fa8853d9f3 |
| Microsoft-Windows-NetworkSecurity | 7b702970-90bc-4584-8b20-c0799086ee5a |
| Microsoft-Windows-Security-SPP-UX | 6bdadc96-673e-468c-9f5b-f382f95b2832 |
| Microsoft-Windows-Security-Auditing | 54849625-5478-4994-a5ba-3e3b0328c30d |
| Microsoft-Windows-Security-LessPrivilegedAppContainer | 45eec9e5-4a1b-5446-7ad8-a4ab1313c437 |
| Microsoft-Windows-Security-UserConsentVerifier | 40783728-8921-45d0-b231-919037b4b4fd |
| Microsoft-Windows-Security-IdentityListener | 3c6c422b-019b-4f48-b67b-f79a3fa8b4ed |
| Microsoft-Windows-Security-EnterpriseData-FileRevocationManager | 2cd58181-0bb6-463e-828a-056ff837f966 |
| Microsoft-Windows-Security-Audit-Configuration-Client | 08466062-aed4-4834-8b04-cddb414504e5 |
| Microsoft-Windows-Security-IdentityStore | 00b7e1df-b469-4c69-9c41-53a6576e3dad |
Triggering a Block Event
Warning: Creating block filters affects other software on the host!
You can immediately clean up with .\WFPSampler.exe -clean.
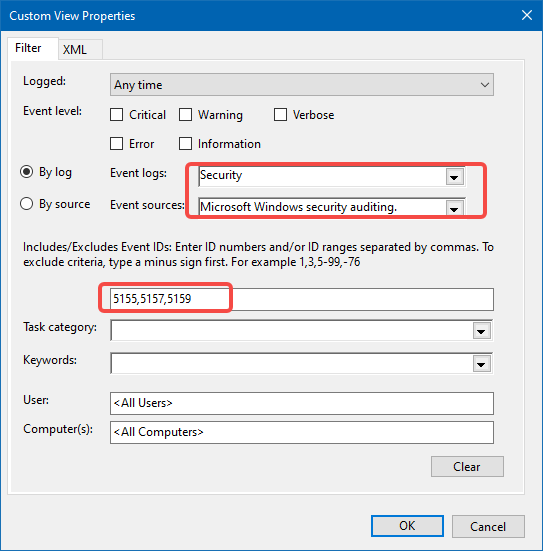
Steps:
Enable auditing for Filtering Platform Connection:
auditpol /set /subcategory:"{0CCE9226-69AE-11D9-BED3-505054503030}" /success:enable /failure:enableOpen Event Viewer, create a Custom View/filter for IDs 5155, 5157, 5159.
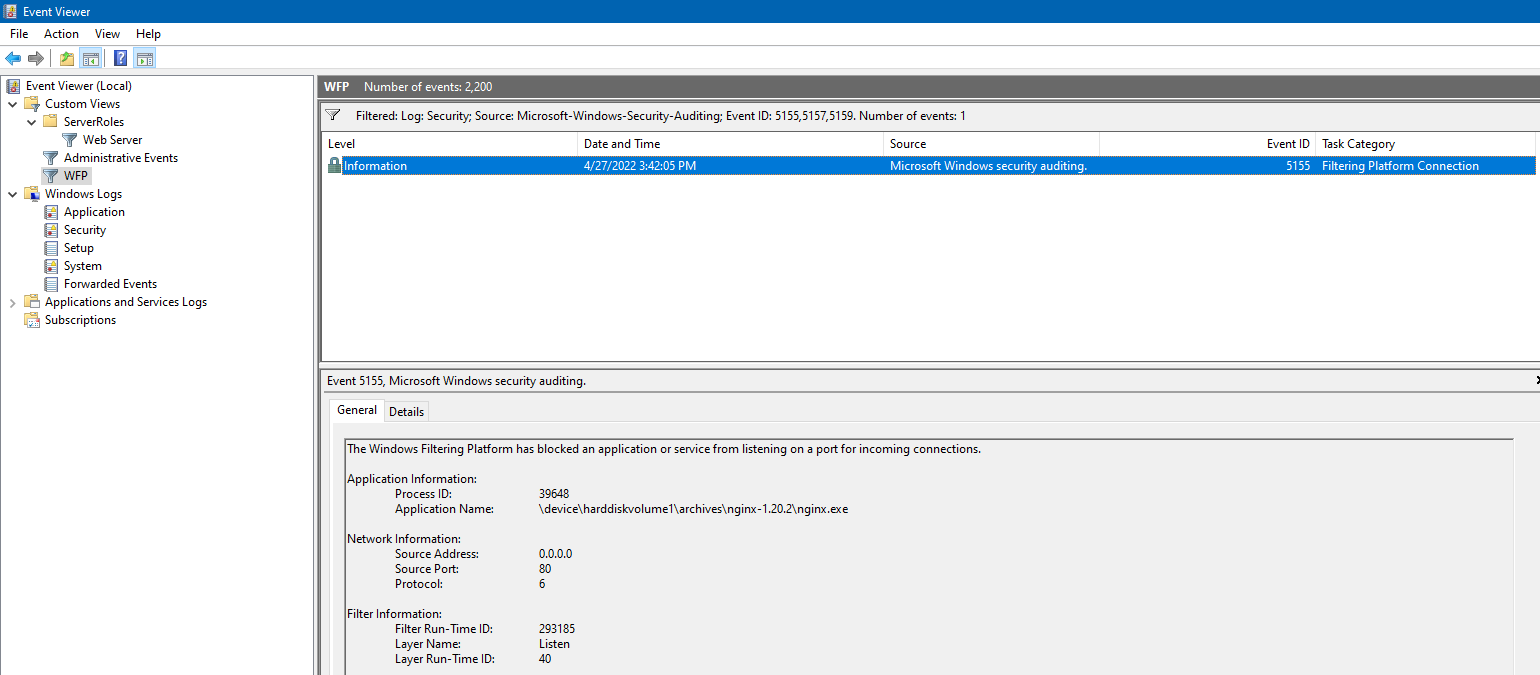
Add a WFP filter using WFPSampler.exe to block listening on port 80:
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_LISTEN_V4 -iplp 80Run a third-party (non-IIS) HTTP server—here we use nginx on port 80. Starting it triggers event 5155.
Clean up the filter:
.\WFPSampler.exe -cleanDisable auditing:
auditpol /set /category:"{0CCE9226-69AE-11D9-BED3-505054503030}" /success:disable /failure:disable
# 5155: an application or service was blocked from listening on a port
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_LISTEN_V4
# 5157: a connection was blocked
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_RECV_ACCEPT_V4
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_CONNECT_V4
# 5159: binding to a local port was blocked
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_RESOURCE_ASSIGNMENT_V4
# Other
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_RESOURCE_ASSIGNMENT_V4_DISCARD
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_RECV_ACCEPT_V4_DISCARD
.\WFPSampler.exe -s BASIC_ACTION_BLOCK -l FWPM_LAYER_ALE_AUTH_CONNECT_V4_DISCARD
# List a WFP filter by ID:
netsh wfp show filters
# Get layer IDs:
netsh wfp show state
Monitoring Network Events (NET_EVENT)
- Events support both enumeration and subscription.
- Enumeration allows filter criteria, querying events within a time window.
- Subscriptions inject a callback to deliver events in real time.
Supported event types:
typedef enum FWPM_NET_EVENT_TYPE_ {
FWPM_NET_EVENT_TYPE_IKEEXT_MM_FAILURE = 0,
FWPM_NET_EVENT_TYPE_IKEEXT_QM_FAILURE,
FWPM_NET_EVENT_TYPE_IKEEXT_EM_FAILURE,
FWPM_NET_EVENT_TYPE_CLASSIFY_DROP,
FWPM_NET_EVENT_TYPE_IPSEC_KERNEL_DROP,
FWPM_NET_EVENT_TYPE_IPSEC_DOSP_DROP,
FWPM_NET_EVENT_TYPE_CLASSIFY_ALLOW,
FWPM_NET_EVENT_TYPE_CAPABILITY_DROP,
FWPM_NET_EVENT_TYPE_CAPABILITY_ALLOW,
FWPM_NET_EVENT_TYPE_CLASSIFY_DROP_MAC,
FWPM_NET_EVENT_TYPE_LPM_PACKET_ARRIVAL,
FWPM_NET_EVENT_TYPE_MAX
} FWPM_NET_EVENT_TYPE;
Enumeration filter fields (FWPM_NET_EVENT_ENUM_TEMPLATE):
| Value | Meaning |
|---|---|
| FWPM_CONDITION_IP_PROTOCOL | The IP protocol number, as specified in RFC 1700. |
| FWPM_CONDITION_IP_LOCAL_ADDRESS | The local IP address. |
| FWPM_CONDITION_IP_REMOTE_ADDRESS | The remote IP address. |
| FWPM_CONDITION_IP_LOCAL_PORT | The local transport protocol port number. For ICMP, the message type. |
| FWPM_CONDITION_IP_REMOTE_PORT | The remote transport protocol port number. For ICMP, the message code. |
| FWPM_CONDITION_SCOPE_ID | The interface IPv6 scope identifier. Reserved for internal use. |
| FWPM_CONDITION_ALE_APP_ID | The full path of the application. |
| FWPM_CONDITION_ALE_USER_ID | The identification of the local user. |
Outside of drivers, only basic drop events are returned.
Monitoring Network Connections (NetConnection)
Compared to monitoring network events, monitoring connections requires higher privileges.
callback approach
The caller needs FWPM_ACTRL_ENUM access to the connection objects’ containers and FWPM_ACTRL_READ access to the connection objects. See Access Control for more information.
Monitoring network connections has not yet succeeded.
I found a similar issue: Receiving in/out traffic stats using WFP user-mode API. It matches the behavior I observed—none of the subscribing functions receive any notifications, giving no events and no errors. Neither enabling auditing nor elevating privileges helped. Some noted that non-kernel mode can only receive drop events, which is insufficient for obtaining block events.
Example of adding a security descriptor: https://docs.microsoft.com/en-us/windows/win32/fwp/reserving-ports
Application Layer Enforcement (ALE) Introduction
- ALE comprises a set of kernel-mode filters that support stateful filtering.
- Filters at the ALE layer can authorize connection creation, port allocation, socket management, raw socket creation, and promiscuous-mode reception.
- Classification of ALE-layer filters is based on the connection or socket; filters in other layers can only classify based on individual packets.
- ALE filter reference: ale-layers
- More filter reference: filtering-layer-identifiers
Coding Notes
Most WFP functions can be invoked from either user mode or kernel mode. However, user-mode functions return a DWORD representing a Win32 error code, whereas kernel-mode functions return an NTSTATUS representing an NT status code.
Therefore, functions share the same names and semantics across modes but have differing signatures. Separate user-mode and kernel-mode headers are required: user-mode header file names end with “u”, and kernel-mode ones end with “k”.
Conclusion
Our requirement is merely to know when events occur; real-time handling is unnecessary, and developing a kernel driver would introduce greater risk. Consequently, we’ll rely on event auditing and monitor event log generation to acquire block events.
A dedicated thread will use NotifyChangeEventLog to watch for new log records.
Appendix
WFP Architecture
WFP (Windows Filter Platform) 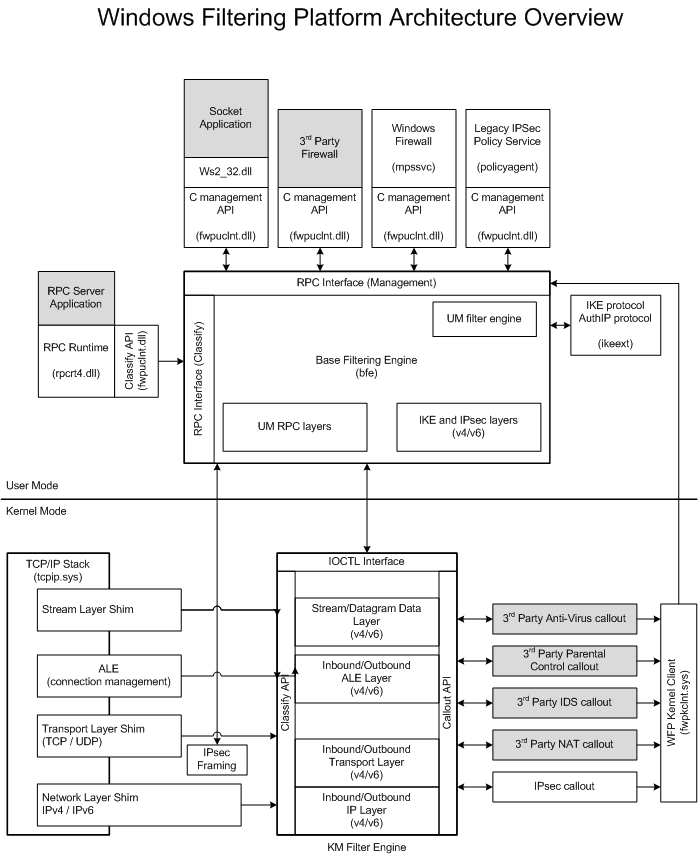
Data Flow
Data flow:
- A packet enters the network stack.
- The network stack finds and invokes a shim.
- The shim initiates classification at a particular layer.
- During classification, filters are matched, and the resulting action is applied. (See Filter Arbitration.)
- If any callout filters match, their corresponding callouts are invoked.
- The shim enforces the final filtering decision (e.g., drop the packet).
Reference Links
Windows Firewall Management – netsh
- Windows Firewall Management – netsh
Windows Firewall Management – netsh
Management Tools
netsh advfirewall
# Export firewall rules
netsh advfirewall export advfirewallpolicy.wfw
# Import firewall rules
netsh advfirewall import advfirewallpolicy.wfw
# View firewall state
netsh advfirewall show allprofiles state
# View firewall default policy
netsh advfirewall show allprofiles firewallpolicy
# netsh advfirewall set allprofiles firewallpolicy blockinbound,allowoutbound
# netsh advfirewall set allprofiles firewallpolicy blockinbound,blockoutbound
# View firewall settings
netsh advfirewall show allprofiles settings
# Enable firewall
netsh advfirewall set allprofiles state on
# Disable firewall
netsh advfirewall set allprofiles state off
# Display firewall rules
netsh advfirewall firewall show rule name=all
# View firewall status
netsh advfirewall monitor show firewall
netsh firewall (deprecated)
# Display firewall state
netsh firewall show state
netsh mbn (Mobile Broadband network)
netsh wfp
# Display firewall state
netsh wfp show state
# Display firewall filters
netsh wfp show filters
Windows Resources
- Windows Resources
Windows Resources Collection
This section lists only some common Windows tools for debugging, troubleshooting, and testing. Tools for packing/unpacking, encryption/decryption, file editors, and programming tools are omitted for brevity.
Tools
Monitoring & Analysis
| Tool Name | Download Link | Description |
|---|---|---|
| DebugView | https://docs.microsoft.com/zh-cn/sysinternals/downloads/debugview | A Sysinternals utility for capturing and controlling kernel and user-mode debug output. |
| Process Monitor | https://docs.microsoft.com/zh-cn/sysinternals/downloads/procmon | A real-time Sysinternals tool that monitors file system, registry, process, thread, and DLL activity to help troubleshoot issues. |
| Process Explorer | https://docs.microsoft.com/zh-cn/sysinternals/downloads/process-explorer | A Sysinternals process viewer that inspects loaded DLLs, call stacks, and which processes have opened a file. |
| WinObj | https://docs.microsoft.com/zh-cn/sysinternals/downloads/winobj | A Sysinternals viewer for the Object Manager namespace; it uses native APIs without loading drivers—see WinObjEx64 for an open-source implementation on GitHub. |
| WinObjEx64 | https://github.com/hfiref0x/WinObjEx64 | An open-source, advanced Object Manager namespace viewer. |
| Handle | https://docs.microsoft.com/zh-cn/sysinternals/downloads/handle | A Sysinternals utility showing which file or directory is held by a running process. |
| Sysinternals Suite | https://live.sysinternals.com/ | The complete suite of Sysinternals utilities—only the most frequently used are listed here to avoid clutter. |
| CPU-Z | https://www.cpuid.com/softwares/cpu-z.html | Real-time CPU monitoring tool. |
| ProcMonX | https://github.com/zodiacon/ProcMonX | An open-source C# implementation using ETW to provide functionality similar to Process Monitor. |
| ProcMonXv2 | https://github.com/zodiacon/ProcMonXv2 | The second open-source C# ETW-based alternative to Process Monitor. |
| Process Hacker | https://github.com/processhacker/processhacker | An open-source Process Explorer-like tool with GPU information support. |
| API Monitor | http://www.rohitab.com/apimonitor | Traces API calls to show how applications/services interact, helps detect bugs, and can modify input/output parameters. |
| Dependency Walker | http://www.dependencywalker.com/ | Scans any 32- or 64-bit Windows module and lists all exported functions. |
| DeviceTree | http://www.osronline.com/article.cfm%5earticle=97.htm | Displays all driver objects and device stack information in the system. |
| Unlocker | https://www.softpedia.com/get/System/System-Miscellaneous/Unlocker.shtml | Unlocks files held by running processes—many similar open-source tools are available. |
| RpcView | https://github.com/silverf0x/RpcView | Shows and decompiles live RPC interfaces on the system—useful when analyzing RPC services. |
| RequestTrace | https://the-sz.com/products/rt/ | Displays IRPs, SRBs, URBs, and related buffers on Windows; mostly redundant as WinDbg covers the same traces but handy without a debugger. |
| IRPMon | https://github.com/MartinDrab/IRPMon | Hooks driver objects to monitor IRP traffic and other driver requests, similar to RequestTrace and IrpTracker. |
| IRPTrace | https://github.com/haidragon/drivertools | Contains a collection of additional tools. |
AntiRootkit Tools
| Tool Name | Download Link | Description |
|---|---|---|
| PcHunter | https://www.anxinsec.com/view/antirootkit/ | Security analysis tool that bypasses rootkits via direct disk, registry, network, etc., showing detailed info on threads, processes, and kernel modules. |
| Windows-Kernel-Explorer | https://github.com/AxtMueller/Windows-Kernel-Explorer | Closed-source alternative to PcHunter, useful when newer OS support is missing. |
| PowerTool | Rarely updated. Developed by a colleague of a friend; reportedly messy codebase. | |
| py | https://github.com/antiwar3/py | PiaoYun ARK—open-source rootkit scanner. |
PE Tools
| Tool Name | Download Link | Description |
|---|---|---|
| CFF Explorer | https://ntcore.com/?page_id=388 | A nice PE explorer. |
| ExeinfoPe | http://www.exeinfo.xn.pl/ | – |
Reverse & Debug
| Tool Name | Download Link | Description | |
|---|---|---|---|
| Ghidra | https://www.nsa.gov/resources/everyone/ghidra/ | A software reverse-engineering (SRE) suite created by the NSA Research Directorate to support cybersecurity missions. | |
| IDA | https://down.52pojie.cn/ | Famous but closed-source interactive disassembler—latest cracks (v7.5) on 52pojie forum. | |
| dnSpy | https://github.com/dnSpy/dnSpy | .NET decompiler; effectively provides source code for unobfuscated .NET binaries if the framework is familiar to you. | |
| OllyDbg | https://down.52pojie.cn/Tools/Debuggers// | Popular debugger with many plugins; closed-source and only for 32-bit binaries. | |
| x64dbg | https://x64dbg.com/ | Open-source debugger for x86/x64 binaries—more convenient than WinDbg yet similar plugin support; recommended over OllyDbg. | |
| Cheat Engine | https://www.cheatengine.org/ | Memory-search & manipulation Swiss-army knife; offers many advanced reverse-engineering features. | |
| VirtualKD-Redux | https://github.com/4d61726b/VirtualKD-Redux/releases | Fully-automated WinDbg virtual-machine debugging without env vars; supports latest VMware. | |
| Driver Loader | http://www.osronline.com/article.cfm%5Earticle=157.htm | OSR tool for installing, loading, and unloading drivers. | |
| reverse-engineering | https://github.com/wtsxDev/reverse-engineering | A curated list of almost every tool you need for reverse engineering. |
Injection Tools
| Tool Name | Download Link | Description | |
|---|---|---|---|
| yapi | https://github.com/ez8-co/yapi | Simple open-source DLL injector for x64/x86 processes—good for learning from the source; supports cross-bit-width injection from 32-bit to 64-bit. | |
| Xenos | https://github.com/DarthTon/Xenos | Open-source injector using the famous Blackbone library; supports kernel-level injection. | |
| ExtremeInjector | https://github.com/master131/ExtremeInjector | Easy-to-use application-layer injector featuring cross-bit-width injection from 32-bit to 64-bit. |
Network
| Tool Name | Download Link | Description |
|---|---|---|
| Fiddler | https://www.telerik.com/fiddler | Powerful HTTPS man-in-the-middle proxy without a certificate hassle; scriptable; ships with an SDK. |
| Wireshark | https://www.wireshark.org/download.html | No introduction needed. |
| Burp Suite | https://portswigger.net/burp | The go-to web proxy for pentesters. Requires JDK; cracked versions available on 52pojie. |
Stress Testing Tools
| Tool Name | Download Link | Description |
|---|---|---|
| Driver Verifier | https://docs.microsoft.com/en-us/windows-hardware/drivers/devtest/driver-verifier | Built-in driver stability and stress tester. |
| Application Verifier | https://docs.microsoft.com/en-us/windows-hardware/drivers/devtest/application-verifier | Built-in application-layer stress tester. |
| CPUStress | https://docs.microsoft.com/en-us/sysinternals/downloads/cpustres | Pushes CPU to full load to test application stability and responsiveness under extreme conditions. |
Others
| Tool Name | Download Link | Description |
|---|---|---|
| game-hacking | https://github.com/dsasmblr/game-hacking | – |
| awesome-malware-analysis | https://github.com/rootkiter/awesome-malware-analysis | Curated list of malware-analysis tools |
| drawio | https://github.com/jgraph/drawio-desktop | The ultimate diagramming tool |
| RazorSQL | https://www.razorsql.com/ | GUI for SQLite3 databases |
| Git Learning Notes | https://github.com/No-Github/1earn/blob/master/1earn/Develop/%E7%89%88%E6%9C%AC%E6%8E%A7%E5%88%B6/Git%E5%AD%A6%E4%B9%A0%E7%AC%94%E8%AE%B0.md | Version management with Git |
| Markdown Syntax Learning | https://github.com/No-Github/1earn/blob/master/1earn/Develop/%E6%A0%87%E8%AE%B0%E8%AF%AD%E8%A8%80/Markdown/Markdown%E8%AF%AD%E6%B3%95%E5%AD%A6%E4%B9%A0.md | Markdown reference |
Code
Operating System
| Tool Name | Download Link | Description |
|---|---|---|
| ReactOS | https://github.com/reactos/reactos | An open-source OS aiming for Windows 2000 driver binary compatibility. |
| wrk-v1.2 | https://github.com/jmcjmmcjc/wrk-v1.2 | Partial Windows NT 5.2 source code. |
| WinNT4 | https://github.com/ZoloZiak/WinNT4 | Windows NT4 kernel source code. |
| whids | https://github.com/0xrawsec/whids/tree/a826d87e0d035daac10bfa96b530c5deff6b9915 | Open source EDR for Windows. |
Kernel Examples
| Tool Name | Download Link | Description |
|---|---|---|
| CPPHelper | https://github.com/Chuyu-Team/CPPHelper | Basic C++ helper class library. |
| cpp_component | https://github.com/skyformat99/cpp_component | Encapsulation of common C/C++ features. |
| WinToolsLib | https://github.com/deeonis-ru/WinToolsLib | Suite of classes for Windows programming. |
| KDU | https://github.com/hfiref0x/KDU | – |
| KTL | https://github.com/MeeSong/KTL | – |
| Kernel-Bridge | https://github.com/HoShiMin/Kernel-Bridge | – |
| KernelForge | https://github.com/killvxk/KernelForge | – |
| ExecutiveCallbackObjects | https://github.com/0xcpu/ExecutiveCallbackObjects | Research on various kernel-mode callbacks. |
| SyscallHook | https://github.com/AnzeLesnik/SyscallHook | System-call hook for Windows 10 20H1. |
| Antivirus_R3_bypass_demo | https://github.com/huoji120/Antivirus_R3_bypass_demo | Eliminates AV via both R3 0-day and R0 0-day. |
| KernelHiddenExecute | https://github.com/zouxianyu/KernelHiddenExecute | Hide code/data in kernel address space. |
| DriverInjectDll | https://github.com/strivexjun/DriverInjectDll | Kernel-mode global and memory-based injection for Win7–Win10. |
| zwhawk | https://github.com/eLoopWoo/zwhawk | Kernel rootkit providing remote command/control. |
| ZeroBank-ring0-bundle | https://github.com/Trietptm-on-Coding-Algorithms/ZeroBank-ring0-bundle | Kernel-mode rootkit for remote server communication. |
| kdmapper | https://github.com/z175/kdmapper | Manual driver mapper (educational/outdated). |
| antispy | https://github.com/mohuihui/antispy | Free but powerful AV & rootkit detection toolkit. |
| windows_kernel_resources | https://github.com/sam-b/windows_kernel_resources | – |
| HookLib | https://github.com/HoShiMin/HookLib | User- and kernel-mode hooking library. |
| Kernel-Whisperer | https://github.com/BrunoMCBraga/Kernel-Whisperer | Kernel module utilities. |
| SQLiteCpp | https://github.com/SRombauts/SQLiteCpp | Smart, easy-to-use C++ SQLite3 wrapper. |
| awesome-windows-kernel-security-development | https://github.com/ExpLife0011/awesome-windows-kernel-security-development | Curated collection of Windows kernel security projects. |
VT Technology
| Tool Name | Download Link | Description |
|---|---|---|
| hvpp | https://github.com/wbenny/hvpp | |
| HyperBone | https://github.com/DarthTon/HyperBone | |
| HyperWin | https://github.com/amiryeshurun/HyperWin | |
| Hypervisor | https://github.com/Bareflank/hypervisor | |
| HyperPlatform | https://github.com/tandasat/HyperPlatform | |
| Hyper-V-Internals | https://github.com/gerhart01/Hyper-V-Internals | |
| Hypervisor-From-Scratch | https://github.com/SinaKarvandi/Hypervisor-From-Scratch | |
| KasperskyHook | https://github.com/iPower/KasperskyHook | |
| awesome-virtualization | https://github.com/Wenzel/awesome-virtualization | |
| ransomware_begone | https://github.com/ofercas/ransomware_begone |
Miscellaneous
| Tool Name | Download Link | Description |
|---|---|---|
| Divert | https://github.com/basil00/Divert | Redirect network traffic to user-mode applications for modification/dropping. |
| Blackbone | https://github.com/DarthTon/Blackbone | Kernel-mode injection techniques, including kernel memory injection. |
| NetWatch | https://github.com/huoji120/NetWatch | Threat-traffic detection platform; supports virtual memory patching. |
| x64_AOB_Search | https://github.com/wanttobeno/x64_AOB_Search | Enterprise-grade high-speed memory scanner (supports wildcards). |
| DuckMemoryScan | https://github.com/huoji120/DuckMemoryScan | Detects most so-called memory-only AV evasion shells. |
| FSDefender | https://github.com/Randomize163/FSDefender | File-system monitoring combined with cloud-backed backups. |
| AntiRansomware | https://github.com/clavis0x/AntiRansomware | Write-scanning anti-ransomware solution—prevents overwriting of files. |
| Lazy | https://github.com/moonAgirl/Lazy | (Malicious) ransomware terminator. |
| awesome-cheatsheets | https://github.com/skywind3000/awesome-cheatsheets/blob/master/tools/git.txt | Handy references for Python, Git, etc. |
CTF Resources
| Repository Name | Repository Link | Description |
|---|---|---|
| CTF-All-In-One | https://github.com/firmianay/CTF-All-In-One | |
| ctf-book | https://github.com/firmianay/ctf-book | Companion resources for the CTF Competition Guide (Pwn Edition). |
Penetration Testing
| Repository Name | Repository Link | Description |
|---|---|---|
| Web-Security-Learning | https://github.com/CHYbeta/Web-Security-Learning | |
| pentest | https://github.com/r0eXpeR/pentest | Tools and project reference for pivoting inside intranets. |
| K8tools | http://k8gege.org/p/72f1fea6.html | Collection of K8tools. |
| Awesome-Red-Teaming | https://github.com/yeyintminthuhtut/Awesome-Red-Teaming | List of Awesome Red-Teaming Resources. |
| Awesome-Hacking | https://github.com/Hack-with-Github/Awesome-Hacking | Curated lists for hackers. |
| awesome-web-hacking | https://github.com/infoslack/awesome-web-hacking | Penetration-testing knowledge base. |
Free Patent Search
| Repository Name | Repository Link | Description |
|---|---|---|
| Patent Information Service Platform | http://search.cnipr.com/ | |
| patents | <www.google.com/patents> | |
| incopat | <www.incopat.com> | |
| Baiten | https://www.baiten.cn/ | |
| rainpat | https://www.rainpat.com/ | |
| Duyan | https://www.uyanip.com/ |
Windows Guide
- Windows Guide
Windows
- [Win-to-go]
- [Understanding Windows File System]
- [Understanding Windows Processes]
- [Windows Related Resources]
- [Advanced Windows Management]
- [Windows Firewall Management - netsh]
- [Blocking Windows Network Traffic Acquisition]
- [Windows Troublesome Issues]
- [Understanding Windows Event Tracing (ETW)]
- [Understanding Windows Networking (WFP)]
- [windows-ipv6-management]
- [IPv6 Issues When Bridging Windows]
- [wireguard configuration]
window-message
- window-message
windows-message
Win-to-go
===
Windows To Go is convenient for portability, but several traditional Windows features are restricted.
- Preface
- Windows To Go Overview
- Differences between Windows To Go and traditional Windows installation
- Using Windows To Go for mobile work
- Preparing to install Windows To Go
- Hardware requirements
- USB hard drive or flash drive
- Host computer
- Checking architecture compatibility between host PC and Windows To Go drive
- Common Windows To Go questions
Preface
Windows To Go has existed for many years, yet there are so few Chinese-language resources on it—one can’t help but worry about the state of domestic IT documentation. The author has limited experience but is exposed to plenty of English development docs and hopes to lay some groundwork for future readers; any mistakes pointed out will be welcomed. For those comfortable reading English, comprehensive official documentation is available at the links below:
- Windows To Go Overview
- Best practice recommendations for Windows To Go
- Deployment considerations for Windows To Go
- Prepare your organization for Windows To Go
- Security and data protection considerations for Windows To Go
- Windows To Go: frequently asked questions
This post covers the overview and some common questions—mostly translations with the occasional author note (indicated by [J] until the next full stop) to prevent misinformation.
Windows To Go Overview
Windows To Go is a feature of Windows Enterprise and Education editions; it is not available in the Home edition used by most general consumers. It allows you to create a portable Windows system on a USB drive or hard disk. Windows To Go is not intended to replace traditional installation methods; its main purpose is to let people who frequently switch workspaces do so more efficiently. Before using Windows To Go, you need to be aware of the following:
- Differences between Windows To Go and traditional Windows installation
- Using Windows To Go for mobile work
- Preparing to install Windows To Go
- Hardware requirements
Differences between Windows To Go and traditional Windows installation
Windows To Go behaves almost like a normal Windows environment except for these differences:
- All internal drives except the USB device you’re running from are offline by default—invisible in File Explorer—to safeguard data. [J]You still have ways to bring those drives online and change their files.
- The Trusted Platform Module (TPM) is unavailable. TPM is tied to an individual PC to protect business data. [J]Most consumer machines don’t have it, but if your corporate laptop is domain-joined, it’s best not to use Windows To Go on it; otherwise, freshen up your résumé first.
- Hibernation is disabled by default in Windows To Go but can be re-enabled via Group Policy. [J]Many machines break USB connections during hibernation and cannot resume—Microsoft anticipated this and disabled it; there’s usually no reason to change that setting.
- Windows Restore is disabled. If the OS breaks, you’ll need to reinstall.
- Factory reset and Windows Reset are unavailable.
- In-place upgrades are not supported. The OS stays at whatever version it was installed as—you cannot go from Windows 7 to 8 or from Windows 10 RS1 to RS2.
Using Windows To Go for mobile work
Windows To Go can boot on multiple machines; the OS will automatically determine the needed drivers. Apps tightly coupled to specific hardware may fail to run. [J]ThinkPad track-pad control apps or fingerprint utilities, for example.
Preparing to install Windows To Go
You can use System Center Configuration Manager or standard Windows deployment tools such as DiskPart and Deployment Image Servicing and Management (DISM). Consider:
- Do you need to inject any drivers into the Windows To Go image?
- How will you store and sync data when switching between machines?
- 32-bit or 64-bit? [J]All new hardware supports 64-bit; 64-bit CPUs can run 32-bit OSes, but 32-bit CPUs cannot run 64-bit OSes. 64-bit systems also consume more disk and memory. If any target machine has a 32-bit CPU or less than 4 GB RAM, stick with 32-bit.
- What resolution should you use when remoting in from external networks?
Hardware requirements
USB hard drive or flash drive
Windows To Go is specifically optimized for certified devices:
- Optimizes USB devices for high random read/write, ensuring smooth daily use.
- Can boot Windows 7 and later from certified devices.
- Continues to enjoy OEM warranty support even while running Windows To Go. [J]The host PC’s warranty wasn’t mentioned.
Uncertified USB devices are not supported. [J]Try it and you’ll learn quickly why—it just won’t work. [J]Non-standard hacks (e.g., spoofing device IDs) are out there but outside scope.
Host computer (Host computer)
- Certified for Windows 7 and later.
- Windows RT systems are unsupported.
- Apple Macs are unsupported. [J]Even though the web is full of success stories on using Windows To Go on a Mac, the official stance is clear: no support.
Minimum specs for a host computer:
| Item | Requirement |
|---|---|
| Boot capability | Must support USB boot |
| Firmware | USB-boot option enabled |
| Processor architecture | Must match supported Windows To Go requirements |
| External USB hub | Not supported. The Windows To Go device must be plugged directly into the host |
| Processor | 1 GHz or faster |
| RAM | 2 GB or more |
| Graphics | DirectX 9 or later with WDDM 1.2 |
| USB port | USB 2.0 or later |
Checking architecture compatibility between host PC and Windows To Go drive
| Host PC Firmware Type | Host PC Processor Architecture | Compatible Windows To Go Image Architecture |
|---|---|---|
| Legacy BIOS | 32-bit | 32-bit only |
| Legacy BIOS | 64-bit | 32-bit and 64-bit |
| UEFI BIOS | 32-bit | 32-bit only |
| UEFI BIOS | 64-bit | 64-bit only |