Certificate Application Issues Caused by CNAME–TXT Conflicts
Categories:
CNAME and TXT Records With the Same Prefix Cannot Coexist
Anyone who has ever configured a domain knows that (A, AAAA) records cannot coexist with a CNAME, but most people have never run into a TXT vs. CNAME conflict.
When would TXT and CNAME need the same prefix?
One scenario occurs while applying for a Let’s Encrypt certificate and using the DNS-01 challenge to prove domain ownership.
- Certbot creates a TXT record for
_acme-challenge.example.com, using an akid/aksecret pair or a token. - Let’s Encrypt queries the TXT record to confirm that the applicant can modify DNS and therefore controls the domain.
- Let’s Encrypt issues the certificate.
- Certbot cleans up the TXT record for
_acme-challenge.example.com.
If a CNAME record for _acme-challenge.example.com already exists when the TXT record is created, the TXT record insertion usually fails, causing the challenge to fail and the certificate to be denied.
Why does a CNAME record like _acme-challenge.example.com ever exist?
Alibaba Cloud recently launched ESA (Edge Security Acceleration), a service similar to Cloudflare and the successor/extension of the original DCDN - Full Site Acceleration.
At first it did not support self-service wildcard certificates, so I ran a periodic script that pushed my own wildcard cert via the ESA API, which was a bit of a hassle.
Later, Managed DCV was introduced, allowing wildcard certs to be requested and renewed automatically.
Following the official docs worked great—suddenly wildcard certs “just worked.”
But the hidden trap only surfaced months later: the persistent CNAME record blocks creation of any TXT record with the same prefix, so I can no longer validate domain ownership elsewhere.
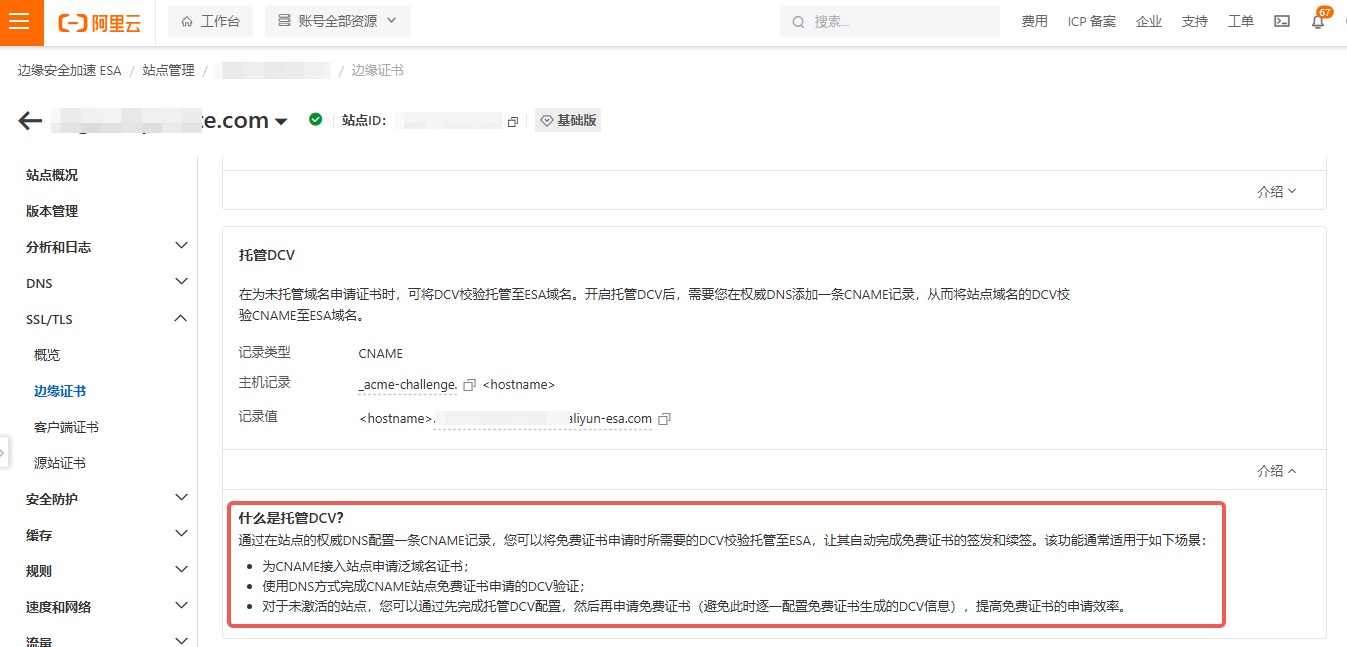
Solutions
Option 1: Stop Using Managed DCV
Managed DCV requires you to point _acme-challenge.example.com to a specific value, which essentially delegates that label (and therefore validates your domain) to a third party—you no longer control it.
If you still need a wildcard certificate, you can task a script to call ESA’s API and upload a new wildcard cert at regular intervals.
Option 2: Switch to a Different Challenge Type
Certbot offers several ways to prove domain ownership:
| Method | Description |
|---|---|
| DNS-01 | Create a TXT record; no prior web server required. |
| HTTP-01 | Place a file on the active web server. |
| TLS-ALPN-01 | Present a special TLS certificate from the server. |
HTTP-01 and TLS-ALPN-01 require a running service before you can get a certificate, whereas DNS-01 works before any services are online.
Option 3: Break Down the Silo Between ESA and Alibaba Cloud DNS
Both products belong to Alibaba Cloud, but they implement separate DNS APIs.
If ESA could create a TXT or CNAME record in Alibaba Cloud DNS, obtain a certificate, and then immediately delete the temporary record, DNS-01 challenges elsewhere would remain unaffected.
Option 4: Leave Alibaba Cloud ESA
Cloudflare doesn’t have this problem—certificates are issued freely without hostname delegation.